Fill the library (AsyncRAT Analysis)
📜Scenario

🔎Solve
We got a mail :
$ sha256sum Return\ book\ loan.eml
d077728db90d22d361d1d9ba161eca474b7e69e9b8415ac2c45cf5430ab1e8c2 Return book loan.eml
Check on VT :
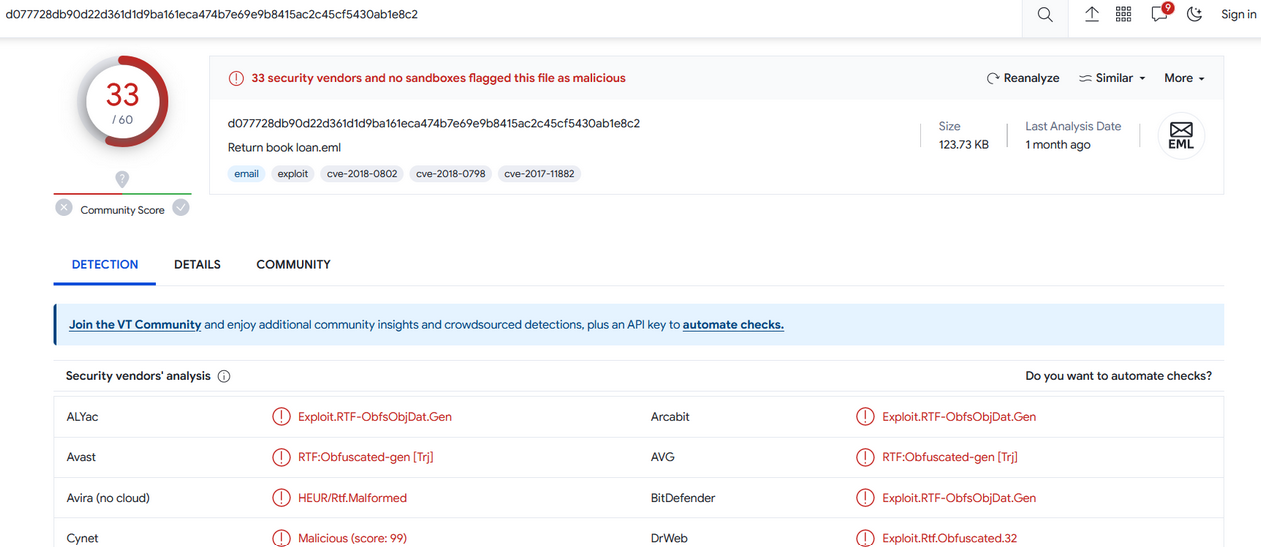
Extract the attachment of the mail and decode it with Cyberchef :
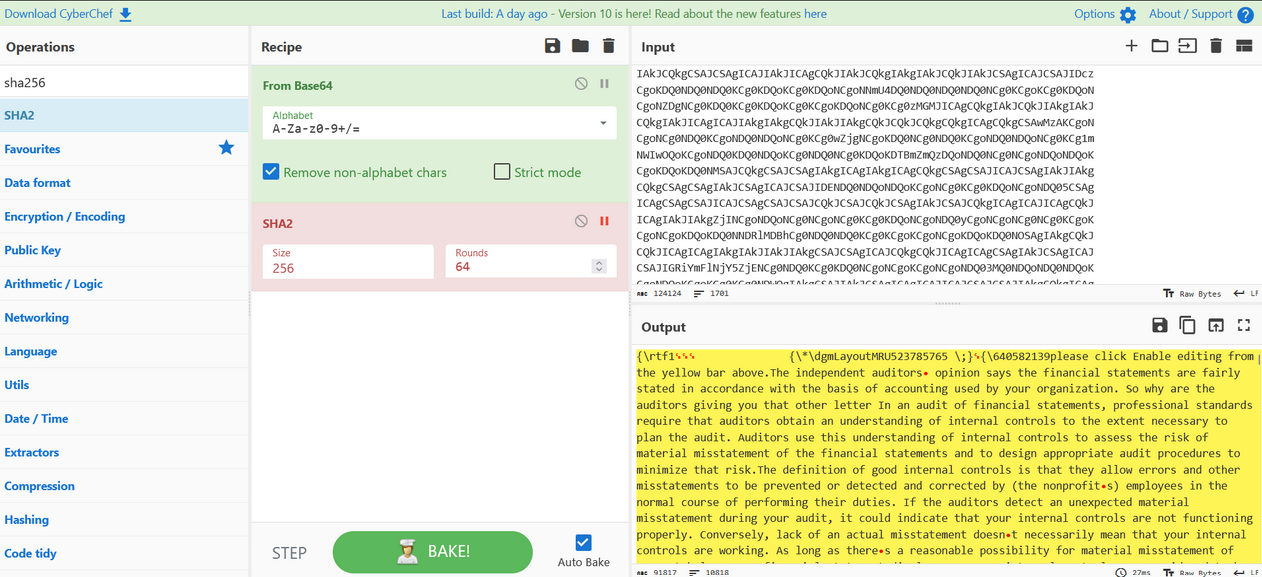
We notice that the file named "Bank details.doc" is in reality a rtf file
We I save the file from Cyberchef on my computer Windows Defender delete it, we could guess that the file signature is known
$ sha256sum download.rtf
8badd7a5fe0794d035783f9afcb7fc3af9a354f3cfb96acb080d3fb53658bb03 download.rtf
Check on VT :
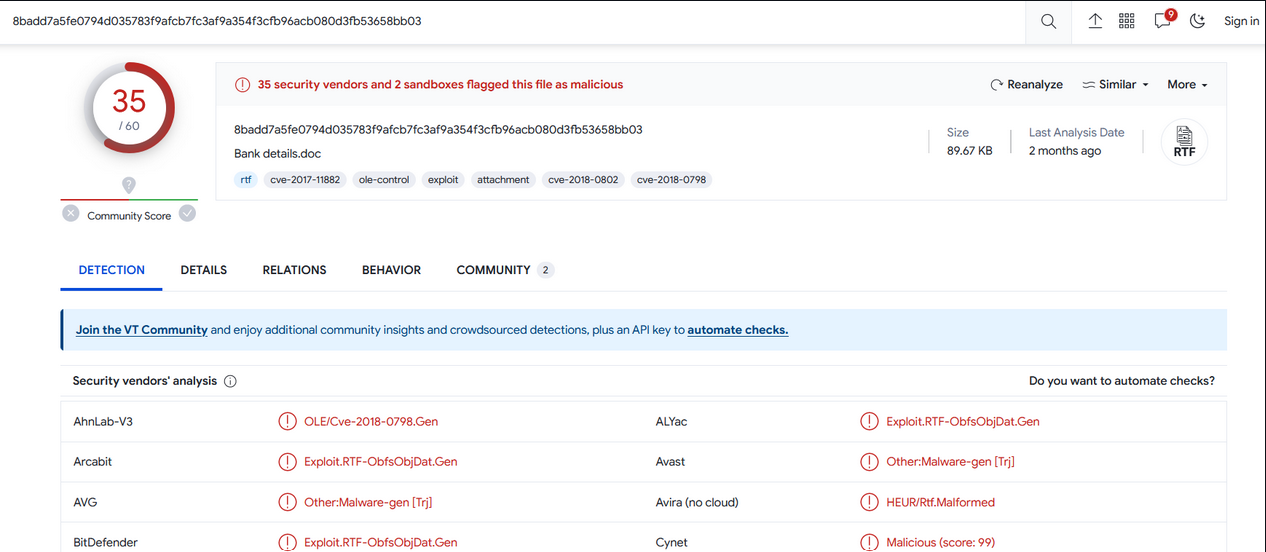
Little check with rtfobj
$ rtfobj download.rtf
rtfobj 0.60.1 on Python 3.11.8 - http://decalage.info/python/oletools
THIS IS WORK IN PROGRESS - Check updates regularly!
Please report any issue at https://github.com/decalage2/oletools/issues
===============================================================================
File: 'download.rtf' - size: 91817 bytes
---+----------+---------------------------------------------------------------
id |index |OLE Object
---+----------+---------------------------------------------------------------
0 |00003183h |Not a well-formed OLE object
---+----------+---------------------------------------------------------------
No OLE info from there :/
So lets analyse it with rtfdump :
$ python2 ../../../DidierStevensSuite/rtfdump.py download.rtf
1 Level 1 c= 2 p=00000000 l= 91815 h= 7545; 18 b= 0 u= 7457 \rtf1
2 Level 2 c= 0 p=0000000d l= 27 h= 10; 9 b= 0 u= 8 \*\dgm
3 Level 2 c= 1 p=0000002b l= 91771 h= 7545; 18 b= 0 u= 7457
4 Level 3 c= 2 p=0000315c l= 79177 h= 3328; 18 b= 0 O u= 0
Name: 'EQuAtIon.3\x00' Size: 1621 md5: e29969b945c96f8cd744f8b38ceb34da magic: 027eb9eb
5 Level 4 c= 0 p=00003183 l= 46 h= 0; 18 b= 0 u= 0 \qmspace903956706
6 Level 4 c= 0 p=000031b4 l= 45 h= 0; 18 b= 0 u= 0 \*\urtf561884577
$ python2 ../../../DidierStevensSuite/rtfdump.py -f O download.rtf
4 Level 3 c= 2 p=0000315c l= 79177 h= 3328; 18 b= 0 O u= 0
Name: 'EQuAtIon.3\x00' Size: 1621 md5: e29969b945c96f8cd744f8b38ceb34da magic: 027eb9eb
$ python2 ../../../DidierStevensSuite/rtfdump.py -s 4 download.rtf
$ python2 ../../../DidierStevensSuite/rtfdump.py -s 4 -Hi download.rtf
Name: 'EQuAtIon.3\x00'
Position embedded: 00000023
Size embedded: 00000655
md5: e29969b945c96f8cd744f8b38ceb34da
magic: 027eb9eb
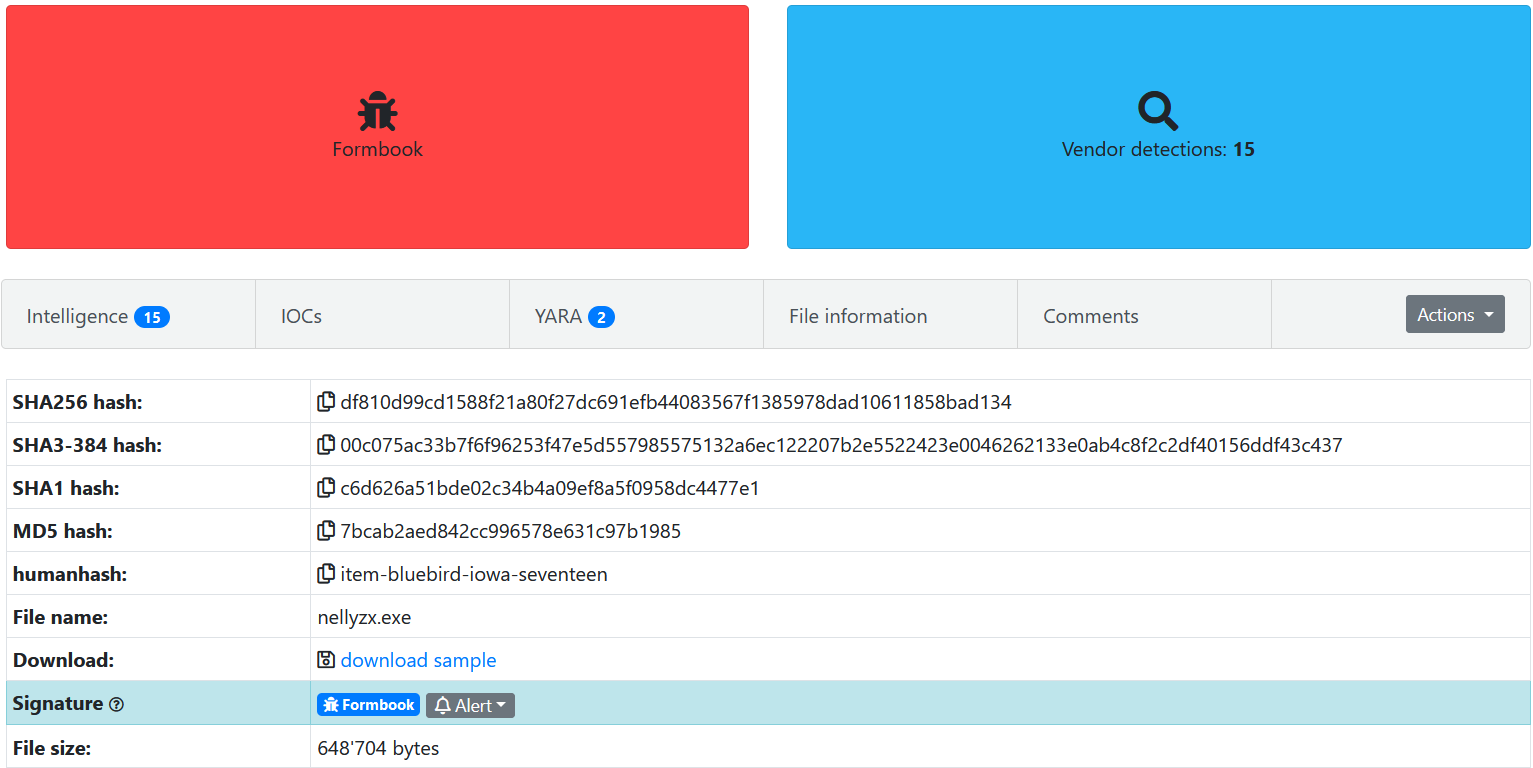
To identify which malware family this sample belongs to, we can navigate to the VirusTotal relationship page and find the URL that communicates with our RTF.
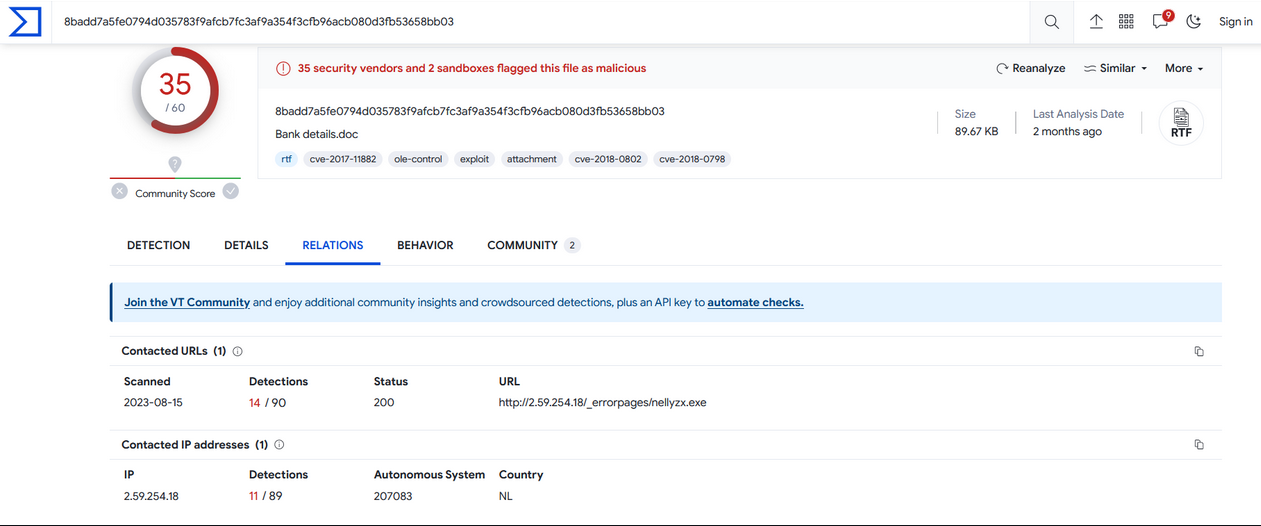
We see that the rtf tries to contact the ip 2.59.254.18 to download the executable nellyzx.exe
By looking on the internet with the keyword nellyzx.exe we found 2 MalwareBazaar Sample and a ZeroBox report :
Many Thanks 🔥
Thanks to my friend from GCC for allowing me to do these challenges for the CTF and thank you to all the participants for their feedback !
NOTE (Edited) :
After the CTF, Crazyman and I had a chat about this chall, in particular about the fact that he had doubts about the sample's attribution.
Indeed, it seems that the pivot made on nellyxz.exe is not correct.
Based on these analyses, I went back to the drawing board to confirm these conclusions.
We therefore start with the .eml file :
d077728db90d22d361d1d9ba161eca474b7e69e9b8415ac2c45cf5430ab1e8c2 Return book loan.eml
Which contains
Bank details.doc -> 8badd7a5fe0794d035783f9afcb7fc3af9a354f3cfb96acb080d3fb53658bb03
rtf
cve-2017-11882
ole-control
exploit
attachment
cve-2018-0802
cve-2018-0798
http://2.59.254.18/_errorpages/nellyzx.exe
According to the VMRay analysis the rtf file drop nellyadh476528.exe

$ sha256sum nellyzx.exe
a636769bcc6e11b5a9be209faa164fc778df5ee6e34ae53a6eeb440314f79929 nellyzx.exe
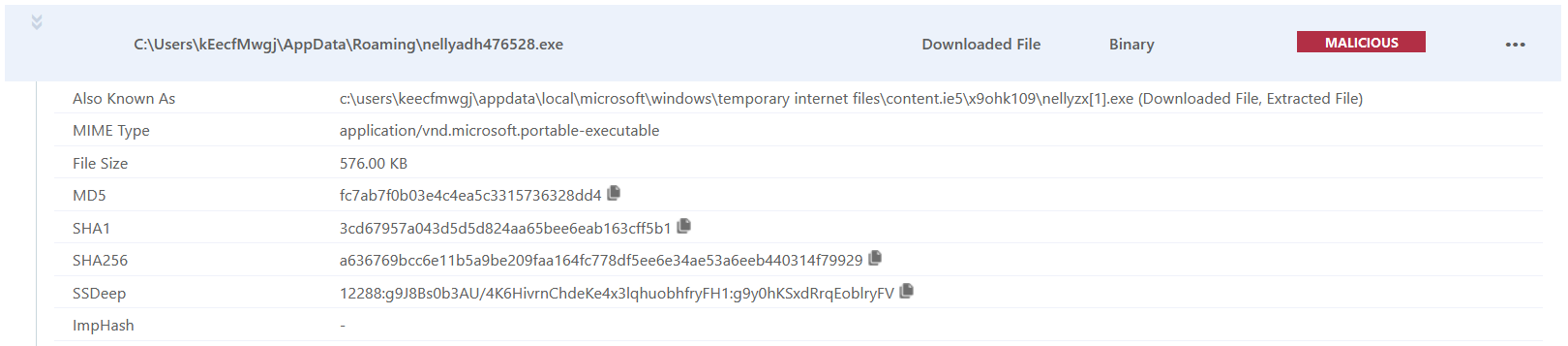
By analyzing the nellyadh476528.exe source code decompile with ilspy
try
{
byte[] array = Decrypt(_assemblyBytes);
File.WriteAllBytes("test.exe", array);
Assembly assembly = Assembly.Load(array);
BerlinCity.ComeOn(assembly)(assembly);
Environment.Exit(0);
}
catch
{
Environment.Exit(0);
}
We can see that nellyadh476528.exe will build an executable named test.exe using the elements it contains.
This gives us :
$ sha256sum test.exe
dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8 test.exe

As shown on the VT graph nellyzx.exe is the parent of test.exe
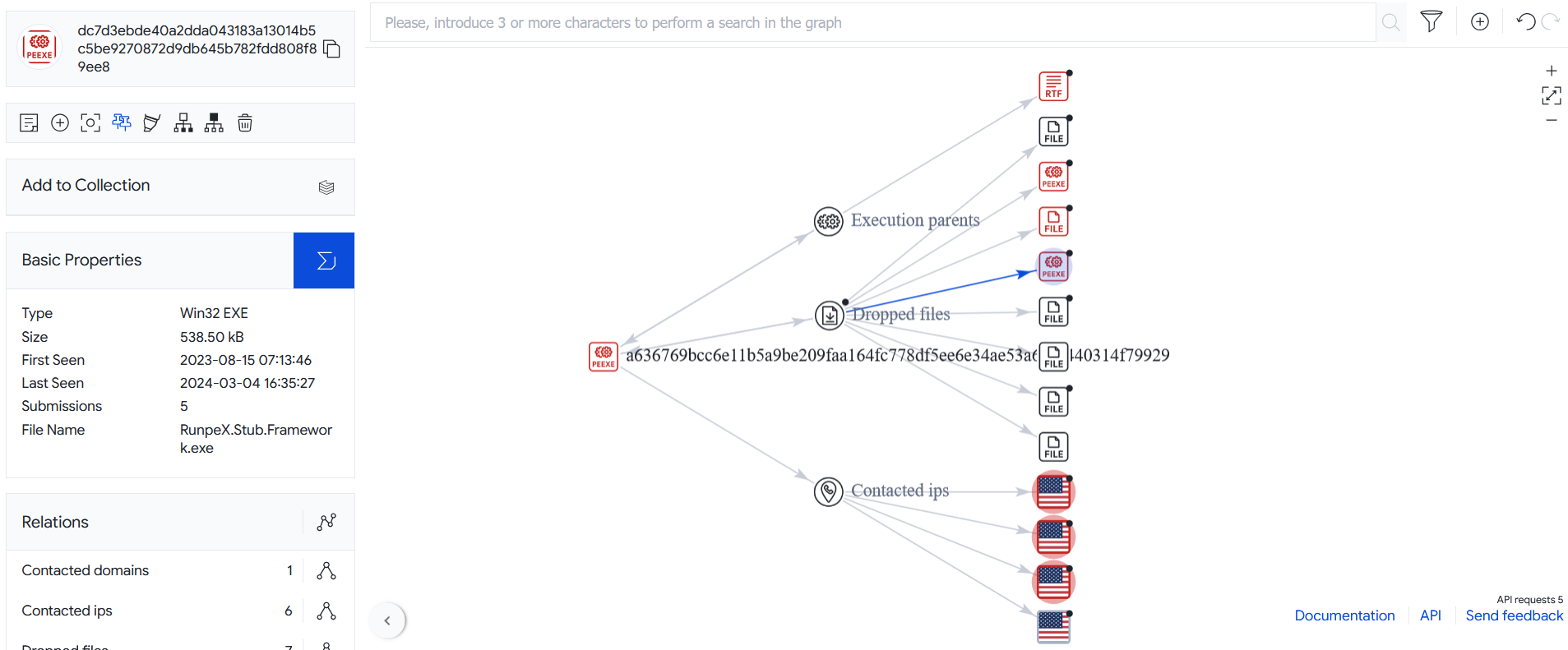
As we can see on to VT we notice that the test.exe is protected by KoiVM(2.0) which obfuscates .NET code
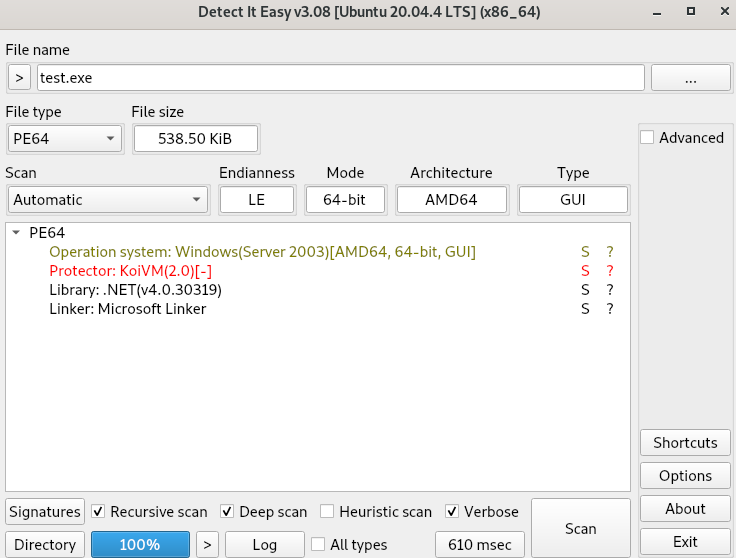
That's drop Zemana.sys with hashs :
$ sha256sum Zemana.sys
543991ca8d1c65113dff039b85ae3f9a87f503daec30f46929fd454bc57e5a91 Zemana.sys
$ sha1sum Zemana.sys
16d7ecf09fc98798a6170e4cef2745e0bee3f5c7 Zemana.sys
According to this CheckPoint Reasearch thread we could say that this sample use CVE-2021-31728 Zemana AntiMalware driver to kill AV/EDR.
There is an article of CheckPoint Reasearch making an analysis of the dotRunpeX injector

They give us a long list of injector samples associated with the different malware families they distribute.
At this point in the analysis, based on the information and screenshots he had shared, crazyman asserted that the sample was part of the AsyncRAT family.
But Injector with the hash dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8 does not appear in the list
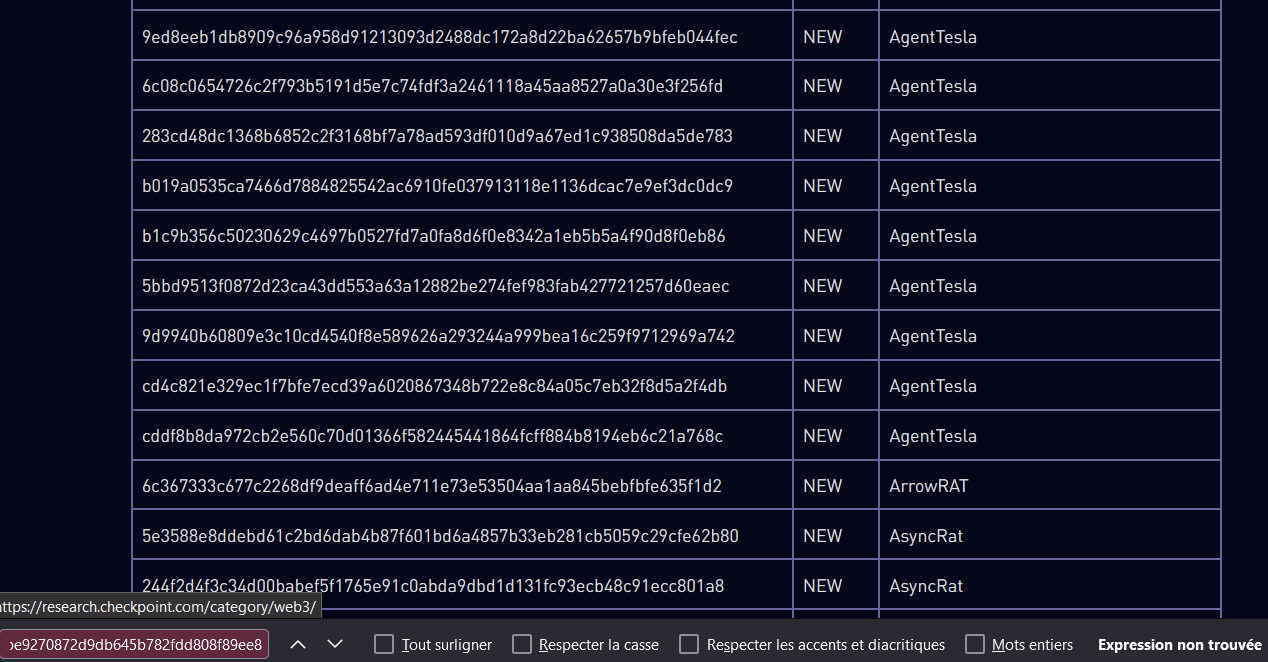
Which means we'll have to dig a little deeper to make sure he belongs.
I think this alert already gives us a first clue 😄
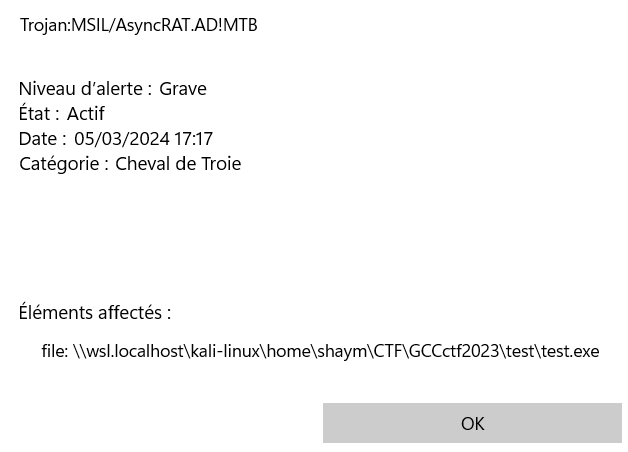
Based on the threatbook sandbox report generated by Crazyman and Github repo of AsyncRAT client source code, we could compare IOCs :
Those observed in the sandbox report :
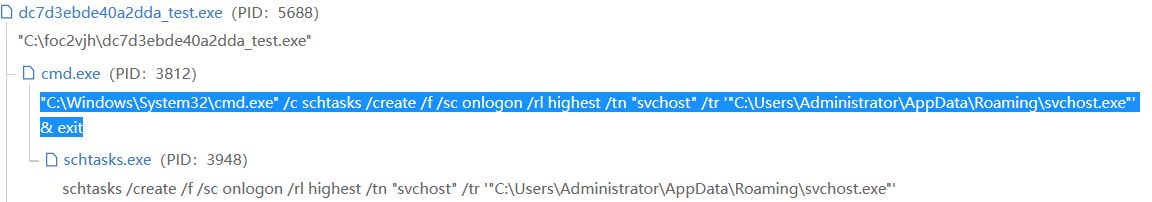
According to crazyman the content, the temporary bat file created looks like this
@echo off
timeout 3>NUL
START "" "C:\Users\Administrator\AppData\Roaming\svchost.exe
CD C:\Users\Administrator\AppData\Local\Temp\
DEL "tmp87FD.tmp.bat"/f /q
Those supposed to be created by the AsyncRAT client
Line 32 to 41
if (Methods.IsAdmin()) //if payload is runnign as administrator install schtasks
{
Process.Start(new ProcessStartInfo
{
FileName = "cmd",
Arguments = "/c schtasks /create /f /sc onlogon /rl highest /tn " + "\"" + Path.GetFileNameWithoutExtension(installPath.Name) + "\"" + " /tr " + "'" + "\"" + installPath.FullName + "\"" + "' & exit",
WindowStyle = ProcessWindowStyle.Hidden,
CreateNoWindow = true,
});
}
Line 62 to 70 :
string batch = Path.GetTempFileName() + ".bat";
using (StreamWriter sw = new StreamWriter(batch))
{
sw.WriteLine("@echo off");
sw.WriteLine("timeout 3 > NUL");
sw.WriteLine("START " + "\"" + "\" " + "\"" + installPath.FullName + "\"");
sw.WriteLine("CD " + Path.GetTempPath());
sw.WriteLine("DEL " + "\"" + Path.GetFileName(batch) + "\"" + " /f /q");
}
We can assume that the sample is part of the AsyncRAT family as assumed at the beginning.
Thanks to crazyman for pointing out the errors in the challs I had created.
The analysis we carried out after the ctf on the sample to identify its real apartenance was very interesting and I learned a lot x)
IOC:
Return book loan.eml - d077728db90d22d361d1d9ba161eca474b7e69e9b8415ac2c45cf5430ab1e8c2
Bank details.doc - 8badd7a5fe0794d035783f9afcb7fc3af9a354f3cfb96acb080d3fb53658bb03
nellyzx.exe - a636769bcc6e11b5a9be209faa164fc778df5ee6e34ae53a6eeb440314f79929
test.exe - dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8
Zemana.sys - 543991ca8d1c65113dff039b85ae3f9a87f503daec30f46929fd454bc57e5a91






