Forensic - Hunt me if you can
📜Scenario
🔎Solve
Quelques recherches sur l’IOC que l’on a extrait du loader JS nous donne ces résultats :
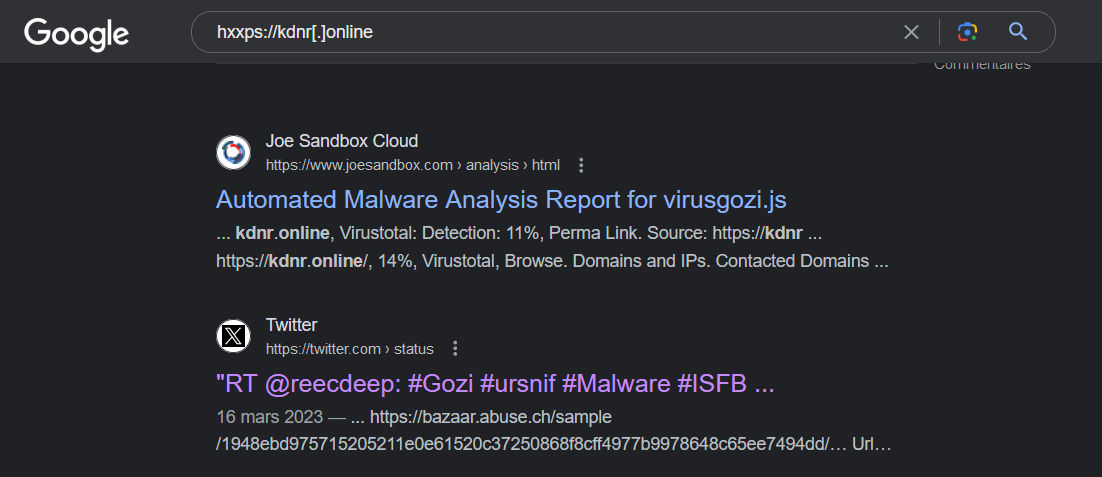
On tombe sur cette chaîne de tweet :
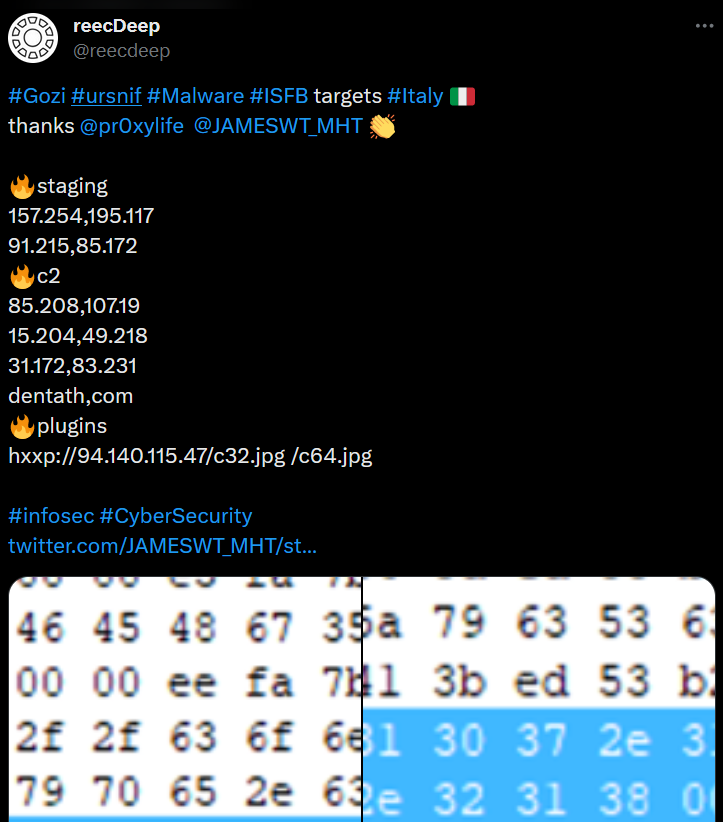
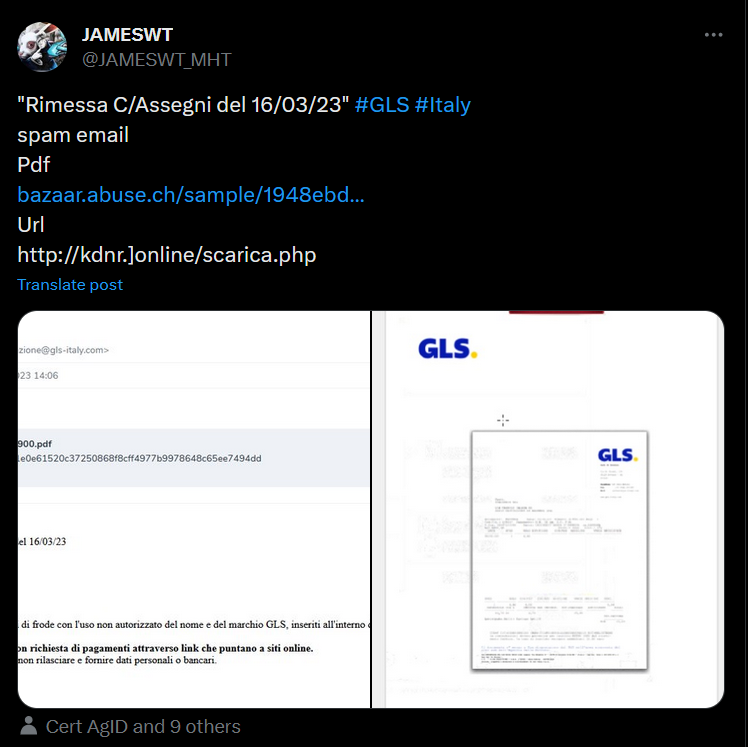
Le lien vers MalwareBazaar redirige vers le sample de RIMESSA_CASSEGNI16032023-2900.pdf en regardant le hash du sample on se rend compte que ce n'est pas celui que nous cherchons.
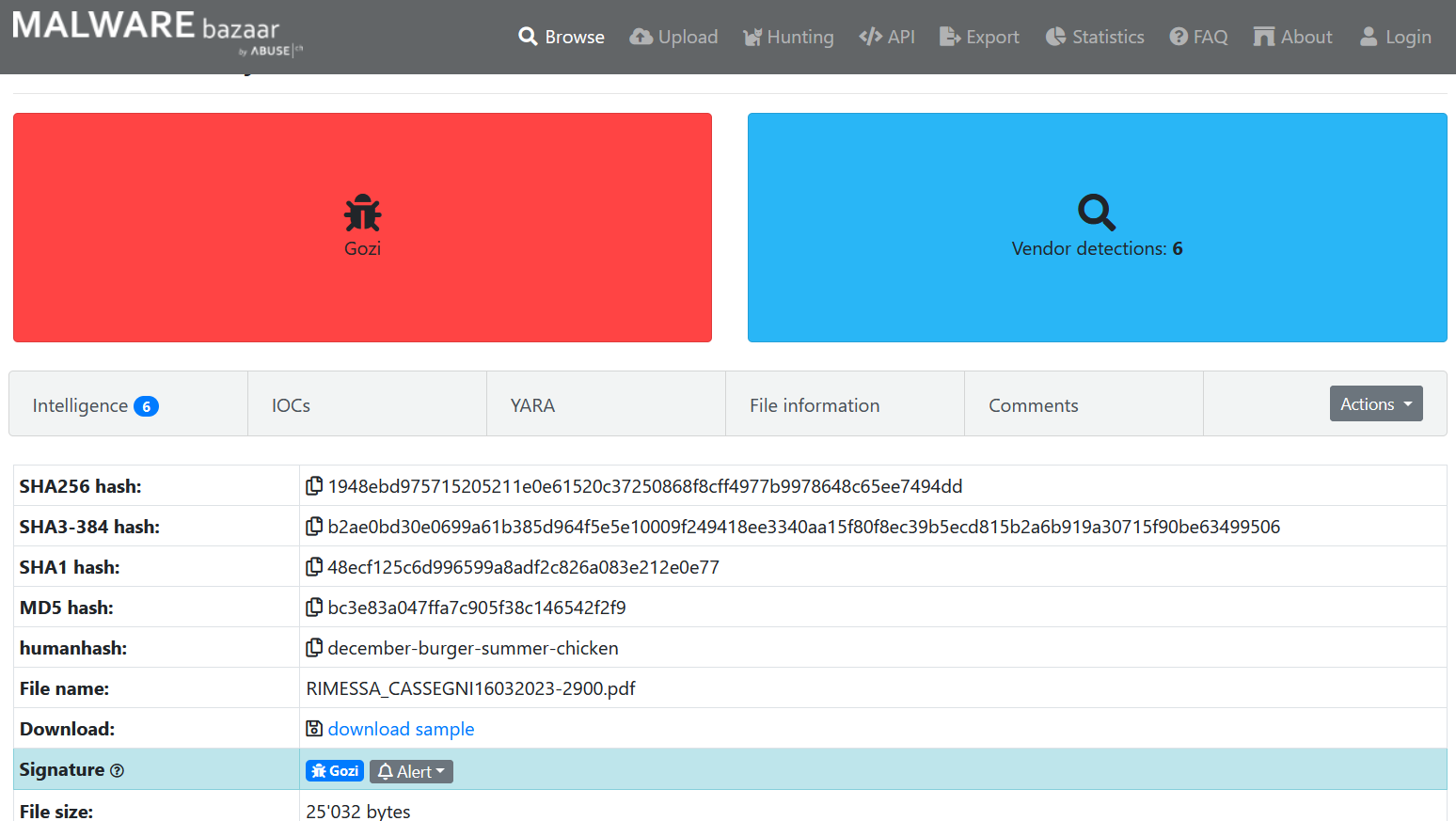
Pour récupérer le hash du fichier on utilise la commande suivante :
$ sha256sum
2a72302c1e76b436da9f0e37941a6e3c1f9921a54bc0bf78d7fe90cf876a6516 message_pour_le_major.txt
On utilise la fonctionnalité Browse de MalwareBazaar avec la query suivante :
sha256:2a72302c1e76b436da9f0e37941a6e3c1f9921a54bc0bf78d7fe90cf876a6516
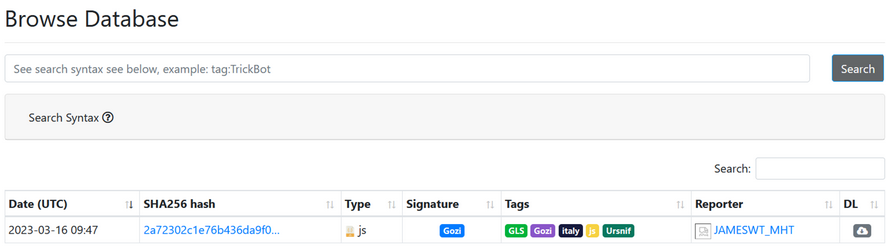
On tombe sur le sample que nous cherchons avec le humanhash suivant : pennsylvania-nuts-foxtrot-uranus
Il s'agit maintenant de faire quelque recherche sur l'histoire du malware. Comme on a pu le constater le malware est appelé Gozi.
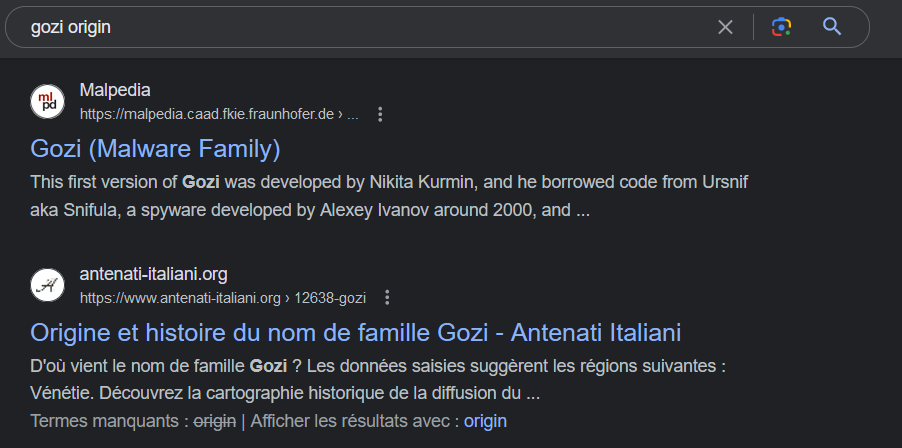
Comme mentionné dans l'article Malpedia :
2000 Ursnif aka Snifula
2006 Gozi v1.0, Gozi CRM, CRM, Papras
2010 Gozi v2.0, Gozi ISFB, ISFB, Pandemyia(*)
-> 2010 Gozi Prinimalka -> Vawtrak/Neverquest
En continuant les recherches, on tombe sur cet article de BlackBerry qui détail un peux plus l'histoire du malware :
What Is Ursnif Malware ?
Ursnif malware (AKA Gozi, Gozi-ISFB, Dreambot, Papras, and snifula) is classified as a banking trojan, stealer, and spyware and was ranked 2020’s second-most active strain of malware, responsible for more than 30 percent of malware detections. Ursnif’s multi-decade lifespan—it first appeared in 2000—makes it one of the oldest malware families. Frequent public source code disclosures have also made it one of the most-forked malware strains. The Ursnif family of malware includes a growing number of highly effective variants with a wide array of modular features. In 2021 Ursnif was highlighted as a top malware strain of concern by the U.S. government’s CISA.
Ursnif Timeline
2000: Ursnif is attributed to the infamous Russian malware developer Alexey Ivanov (AKA subbsta)
2006: Ursnif stealer capabilities were combined with botnet and command and control (C2) functions from the malware Nuclear Grabber to create Gozi
2010: New version Gozi-ISFB emerges from leaked Gozi source code and becomes the dominant Ursnif strain
2014: Dreambot, a Ursnif variant that allows operation over the TOR network, emerges and remains popular until 2020
2014: Vawtrak (AKA Catch, grabnew, NeverQuest) appears. Though based on the original Gozi code, it gets forked extensively into its successful banking trojan with VNC remote desktop to surveil targets and steal data, as well as sophisticated web injects to steal session credentials and MFA tokens from users logging into banking and crypto sites
2016: GozNym banking malware combines the stealth of malware strain Nymaim and the capabilities of Ursnif’s Gozi-ISFB strain. In 2019, it instigated an unprecedented international law enforcement operation by Europol
2020: LOLsnif (AKA Goziat), named for its “Living Off the Land” detection evasion technique, increases Ursnif’s prominence
On identifie donc que le nom d'origine du banking malware Gozi est Ursnif. Ce qui est cohérent si on regarde les # Twitter vu plus tôt.
NBCTF{ursnif:three-georgia-xray-jig}
✏️Note
L'ensemble des ressources mentionné dans ce WriteUp peuvent vous être utiles pour commencer une veille cyber.
WriteUp and Chall made by Shaym



