Down the Wormhole
📜Scenario
🔎Solve
Lets start with the file wormhole.jpg.
First thing we could do is to check the exif metadata.
$ exiftool wormhole.jpg
ExifTool Version Number : 12.67
File Name : wormhole.jpg
Directory : .
File Size : 1341 kB
File Modification Date/Time : 2023:10:28 14:49:09+02:00
File Access Date/Time : 2023:10:28 14:53:24+02:00
File Inode Change Date/Time : 2023:10:28 14:53:19+02:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Comment : cGFzc3dvcmQ6IGRpZ2dpbmdkZWVwZXI=
Image Width : 3840
Image Height : 2160
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 3840x2160
Megapixels : 8.3
We noticed that the Comment field contain a strange Base64 string that we could decode
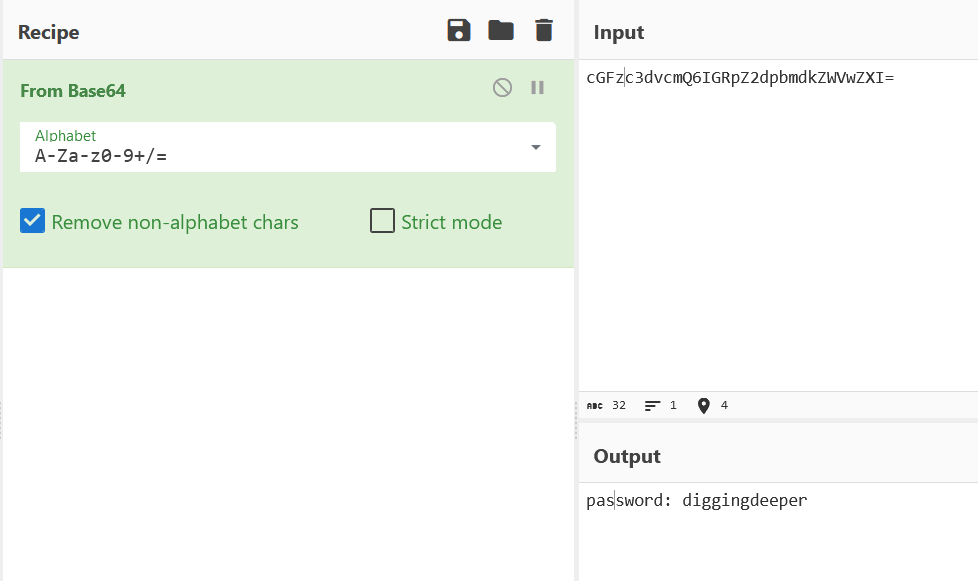
After that we could use steghide to extract hidden data in the picture with this password
$ steghide extract -sf wormhole.jpg
Enter passphrase:
wrote extracted data to "next.txt"..
$ cat next.txt
After diving through the wormhole, you find yourself in front of a rabbit hole. What secrets lie inside?
https://niccgetsspooky.xyz/r/a/b/b/i/t/h/o/l/e/rabbit-hole.svg
We follow the rabbit in the hole and find that

Get the source code with CTRL + U
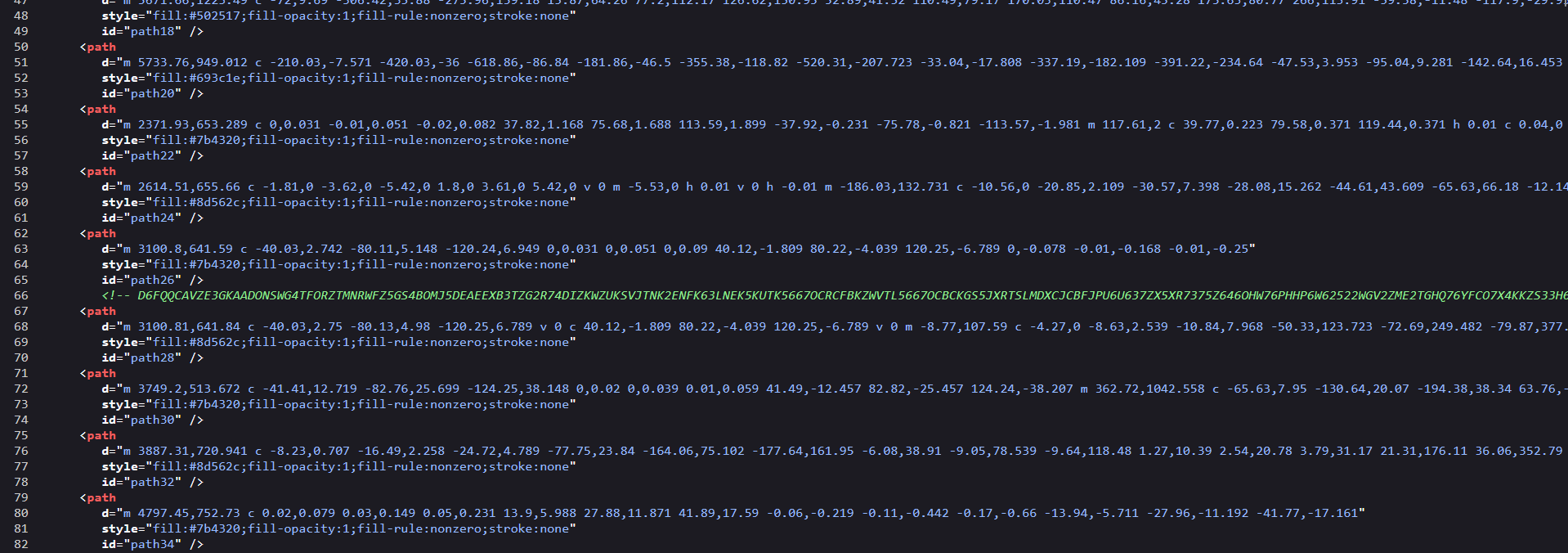
We find this strange comment that we put in CyberChef, he cook well !
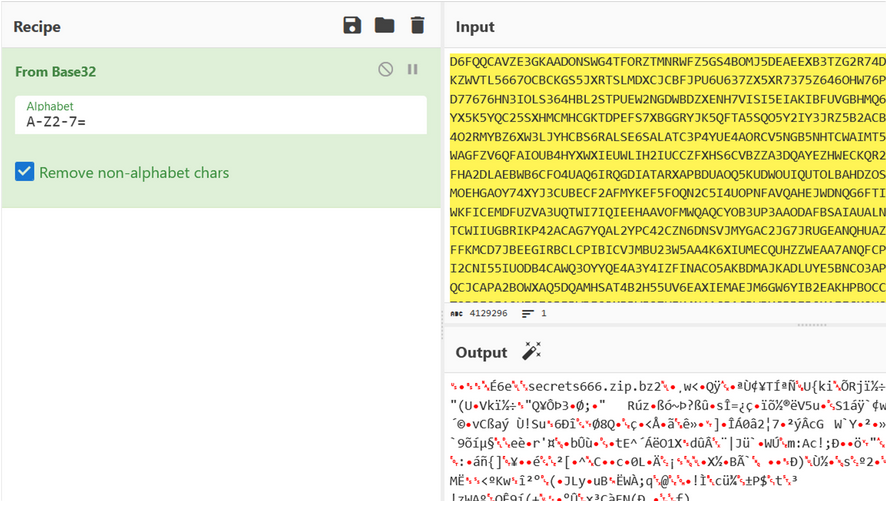
As we can see the file found in the rabbit hole is a Gzip file that contain a file named secrets666.zip.bz2
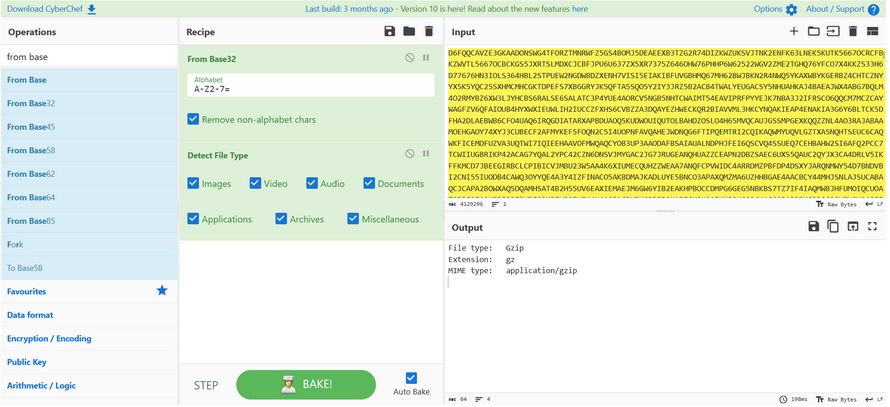
We get download.gz
$ file download.gz
download.gz: gzip compressed data, was "secrets666.zip.bz2", last modified: Mon Oct 23 19:27:17 2023, from Unix, original size modulo 2^32 2580711
$ gzip -d download.gz
$ file download
download: bzip2 compressed data, block size = 900k
$ bzip2 -d download
bzip2: Can't guess original name for download -- using download.out
$ file download.out
download.out: Zip archive data, at least v2.0 to extract, compression method=deflate
$ unzip download.out
Archive: download.out
inflating: secrets665.zip.bz2.gz
Okay we can see some interesting pattern, it looks like we are dealing with a zip bomb.
The compression format is zip > bz2 > gz
So to obtain the flag we just need to do the reverse operation 666 times to obtain the content of secret666 xD
Let's script this !
import os
import gzip
import bz2
import zipfile
def recursive_extract(filename):
print(filename)
if filename.endswith('.zip'):
with zipfile.ZipFile(filename, 'r') as zip_file:
zip_file.extractall()
for name in zip_file.namelist():
recursive_extract(name)
elif filename.endswith('.bz2'):
with open(filename, 'rb') as f:
decompressed = bz2.decompress(f.read())
with open(filename[:-4], 'wb') as f_out:
f_out.write(decompressed)
os.remove(filename)
recursive_extract(filename[:-4])
elif filename.endswith('.gz'):
with open(filename, 'rb') as f:
decompressed = gzip.decompress(f.read())
with open(filename[:-3], 'wb') as f_out:
f_out.write(decompressed)
os.remove(filename)
recursive_extract(filename[:-3])
# Le nom de votre fichier initial
#initial_file = 'secrets665.zip'
#initial_file = 'secrets8364.zip'
initial_file = 'secrets8.zip'
recursive_extract(initial_file)
NOTE : because of recursive python errors we have to restart the script sometimes but it works
Small excerpt
$ ls bomb/
flag.txt secrets167.zip secrets234.zip secrets301.zip secrets36.zip secrets437.zip secrets504.zip secrets572.zip secrets63.zip
secrets0.zip secrets168.zip secrets235.zip secrets302.zip secrets370.zip secrets438.zip secrets505.zip secrets573.zip secrets640.zip
secrets100.zip secrets169.zip secrets236.zip secrets303.zip secrets371.zip secrets439.zip secrets506.zip secrets574.zip secrets641.zip
secrets101.zip secrets16.zip secrets237.zip secrets304.zip secrets372.zip
secrets165.zip secrets232.zip secrets2.zip secrets368.zip secrets435.zip secrets502.zip secrets570.zip secrets638.zip
secrets166.zip secrets233.zip secrets300.zip secrets369.zip secrets436.zip secrets503.zip secrets571.zip secrets639.zip
$ cat bomb/flag.txt
NICC{TH3-UF0S-4R3-UP-N0T-D0WN-50-WHY-4R3-Y0U-D0WN-H3R3}
WriteUp made by Shaym




