Phanpyware
📜Scenario
🔎Solve
Firstly, we will identify the memory capture that we have in front of us.
python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.info
Variable Value
Kernel Base 0xf80137400000
DTB 0x1aa000
Symbols file:///home/shaym/volatility3/volatility3/symbols/windows/ntkrnlmp.pdb/9F65CD18C2F36F88B2D0CE8A7BFE2BB7-1.json.xz
Is64Bit True
IsPAE False
layer_name 0 WindowsIntel32e
memory_layer 1 FileLayer
KdVersionBlock 0xf8013800f400
Major/Minor 15.19041
MachineType 34404
KeNumberProcessors 6
SystemTime 2024-09-17 13:53:31
NtSystemRoot C:\Windows
NtProductType NtProductWinNt
NtMajorVersion 10
NtMinorVersion 0
PE MajorOperatingSystemVersion 10
PE MinorOperatingSystemVersion 0
PE Machine 34404
PE TimeDateStamp Fri Dec 26 20:27:08 2003
Once the profile is identified, we identify the processes running on the machine to try to identify the malicious process
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.pstree
Volatility 3 Framework 2.5.1
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
4 0 System 0xae03b387d040 155 - N/A False 2024-09-17 13:48:44.000000 N/A
* 412 4 smss.exe 0xae03b56ee040 2 - N/A False 2024-09-17 13:48:44.000000 N/A
* 124 4 Registry 0xae03b39e0040 4 - N/A False 2024-09-17 13:48:41.000000 N/A
* 1772 4 MemCompression 0xae03bae56040 42 - N/A False 2024-09-17 13:48:52.000000 N/A
520 504 csrss.exe 0xae03b6786080 10 - 0 False 2024-09-17 13:48:50.000000 N/A
596 588 csrss.exe 0xae03b6c20140 12 - 1 False 2024-09-17 13:48:50.000000 N/A
616 504 wininit.exe 0xae03b6948080 1 - 0 False 2024-09-17 13:48:50.000000 N/A
** 868 740 svchost.exe 0xae03b6c7f240 15 - 0 False 2024-09-17 13:48:51.000000 N/A
*** 5952 868 StartMenuExper 0xae03bc8e90c0 6 - 1 False 2024-09-17 13:49:44.000000 N/A
*** 7104 868 WmiPrvSE.exe 0xae03bc0f1080 4 - 0 False 2024-09-17 13:52:57.000000 N/A
*** 1604 868 TextInputHost. 0xae03bd94c080 13 - 1 False 2024-09-17 13:50:58.000000 N/A
*** 6952 868 SearchApp.exe 0xae03b58090c0 36 - 1 False 2024-09-17 13:49:47.000000 N/A
*** 8044 868 RuntimeBroker. 0xae03b5b8e080 6 - 1 False 2024-09-17 13:49:59.000000 N/A
*** 4460 868 FileCoAuth.exe 0xae03bbc42300 4 - 1 False 2024-09-17 13:52:26.000000 N/A
*** 3504 868 dllhost.exe 0xae03bb52b2c0 4 - 0 False 2024-09-17 13:48:58.000000 N/A
*** 6100 868 RuntimeBroker. 0xae03bc99c080 4 - 1 False 2024-09-17 13:49:45.000000 N/A
*** 4984 868 PhoneExperienc 0xae03bc989080 19 - 1 False 2024-09-17 13:54:07.000000 N/A
*** 7160 868 RuntimeBroker. 0xae03bcc2b080 10 - 1 False 2024-09-17 13:49:47.000000 N/A
** 5732 740 svchost.exe 0xae03b66cf080 11 - 1 False 2024-09-17 13:51:03.000000 N/A
** 1000 740 svchost.exe 0xae03b6d1f2c0 8 - 0 False 2024-09-17 13:48:51.000000 N/A
** 1644 740 svchost.exe 0xae03b6fea240 8 - 0 False 2024-09-17 13:48:52.000000 N/A
*** 4720 1644 MicrosoftEdgeU 0xae03bbff0080 5 - 0 True 2024-09-17 13:49:36.000000 N/A
*** 4796 1644 taskhostw.exe 0xae03bc4aa080 0 - 1 False 2024-09-17 13:49:36.000000 2024-09-17 13:49:37.000000
*** 4336 1644 taskhostw.exe 0xae03bc5430c0 8 - 1 False 2024-09-17 13:49:36.000000 N/A
** 4076 740 svchost.exe 0xae03bba0c300 1 - 0 False 2024-09-17 13:49:03.000000 N/A
** 8172 740 SecurityHealth 0xae03bbc76300 8 - 0 False 2024-09-17 13:50:05.000000 N/A
** 3568 740 svchost.exe 0xae03bb5b0080 25 - 0 False 2024-09-17 13:48:59.000000 N/A
** 2548 740 svchost.exe 0xae03bb0d3300 14 - 0 False 2024-09-17 13:48:54.000000 N/A
** 2804 740 svchost.exe 0xae03bb24a2c0 16 - 0 False 2024-09-17 13:48:54.000000 N/A
** 7668 740 svchost.exe 0xae03b5b6c240 4 - 0 False 2024-09-17 13:49:52.000000 N/A
** 628 740 svchost.exe 0xae03b5ad4240 3 - 0 False 2024-09-17 13:50:07.000000 N/A
** 1016 740 svchost.exe 0xae03b6dd4080 7 - 0 False 2024-09-17 13:48:52.000000 N/A
** 9076 740 svchost.exe 0xae03bd9eb080 8 - 0 False 2024-09-17 13:51:03.000000 N/A
** 4604 740 svchost.exe 0xae03bc3f3080 5 - 1 False 2024-09-17 13:49:36.000000 N/A
668 588 winlogon.exe 0xae03b6c24080 4 - 1 False 2024-09-17 13:48:50.000000 N/A
* 4300 668 userinit.exe 0xae03bc563080 0 - 1 False 2024-09-17 13:49:37.000000 2024-09-17 13:50:02.000000
** 4164 4300 explorer.exe 0xae03bc638080 96 - 1 False 2024-09-17 13:49:38.000000 N/A
*** 7520 4164 VBoxTray.exe 0xae03bb97a080 13 - 1 False 2024-09-17 13:50:06.000000 N/A
*** 636 4164 msedge.exe 0xae03b5ad20c0 46 - 1 False 2024-09-17 13:50:07.000000 N/A
**** 836 636 msedge.exe 0xae03bb0c2080 18 - 1 False 2024-09-17 13:52:04.000000 N/A
**** 3900 636 msedge.exe 0xae03bd2a4340 18 - 1 False 2024-09-17 13:51:50.000000 N/A
**** 6184 636 msedge.exe 0xae03b66e1080 9 - 1 False 2024-09-17 13:50:10.000000 N/A
**** 1548 636 msedge.exe 0xae03b582f080 11 - 1 False 2024-09-17 13:50:11.000000 N/A
**** 4268 636 msedge.exe 0xae03bc986080 13 - 1 False 2024-09-17 13:51:17.000000 N/A
**** 8268 636 msedge.exe 0xae03bbaf3080 18 - 1 False 2024-09-17 13:51:37.000000 N/A
**** 6672 636 msedge.exe 0xae03b5d32080 20 - 1 False 2024-09-17 13:50:10.000000 N/A
**** 6740 636 msedge.exe 0xae03b668d080 22 - 1 False 2024-09-17 13:50:10.000000 N/A
**** 6804 636 msedge.exe 0xae03b5833080 20 - 1 False 2024-09-17 13:50:15.000000 N/A
**** 7764 636 msedge.exe 0xae03bcddc080 18 - 1 False 2024-09-17 13:52:04.000000 N/A
**** 1500 636 msedge.exe 0xae03bb0cb080 15 - 1 False 2024-09-17 13:52:21.000000 N/A
**** 4508 636 msedge.exe 0xae03bbde0080 21 - 1 False 2024-09-17 13:50:14.000000 N/A
*** 2180 4164 FTK Imager.exe 0xae03b5835080 15 - 1 False 2024-09-17 13:50:13.000000 N/A
*** 8140 4164 SecurityHealth 0xae03b6db02c0 3 - 1 False 2024-09-17 13:50:05.000000 N/A
*** 7548 4164 OneDrive.exe 0xae03bba38080 24 - 1 False 2024-09-17 13:50:06.000000 N/A
* 908 668 fontdrvhost.ex 0xae03b6ca5140 5 - 1 False 2024-09-17 13:48:51.000000 N/A
* 780 668 dwm.exe 0xae03b6db3080 20 - 1 False 2024-09-17 13:48:51.000000 N/A
5068 7964 Discord.exe 0xae03bd9dc0c0 53 - 1 False 2024-09-17 13:50:20.000000 N/A
* 8128 5068 Discord.exe 0xae03bd994080 9 - 1 False 2024-09-17 13:50:22.000000 N/A
* 8800 5068 Discord.exe 0xae03bd9aa0c0 9 - 1 False 2024-09-17 13:50:40.000000 N/A
* 7280 5068 Discord.exe 0xae03b66c00c0 17 - 1 False 2024-09-17 13:50:23.000000 N/A
* 7256 5068 Discord.exe 0xae03bd9990c0 21 - 1 False 2024-09-17 13:50:23.000000 N/A
* 8508 5068 Discord.exe 0xae03bba08080 35 - 1 False 2024-09-17 13:50:32.000000 N/A
6088 5080 free-robux.exe 0xae03bb594080 1 - 1 False 2024-09-17 13:52:58.000000 N/A
* 8792 6088 free-robux.exe 0xae03bb0b8340 1 - 1 False 2024-09-17 13:52:59.000000 N/A
We identify two processes which are unusual free-robux.exe especially since roblox is a game known to be used by malicious actors as a vector of compromise.
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.cmdline
Volatility 3 Framework 2.5.1
Progress: 100.00 PDB scanning finished
PID Process Args
4 System Required memory at 0x20 is not valid (process exited?)
124 Registry Required memory at 0x20 is not valid (process exited?)
6088 free-robux.exe "C:\Users\bipbop\Downloads\free-robux.exe" C:\Users\bipbop\AppData\Local\Temp\_MEI79202\phanpy.py
8792 free-robux.exe "C:\Users\bipbop\Downloads\free-robux.exe" C:\Users\bipbop\AppData\Local\Temp\_MEI79202\phanpy.py
3620 SearchFilterHo "C:\Windows\system32\SearchFilterHost.exe" 0 860 864 872 8192 868 840
the command history tells us that the first stage of the malware uses python scripts, however no trace in the filescan. So I didn't dig the trail any further.
While searching for interesting files in the victim's file system, I came across these 3 text files. Unfortunately the two files containing secrets seem to be encrypted or are in any case unusable as they stand.
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.filescan | grep -i ".txt"
0xae03bbb1ce00 \Users\bipbop\Documents\Homework\friend-secret.txt 216
0xae03bb866940 \Users\bipbop\Documents\password.txt 216
0xae03bd44fd00 \Users\bipbop\Desktop\Ph4nPy.readme.txt 216
So I focused on the README
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.dumpfiles --virtaddr 0xae03bd44fd00
Volatility 3 Framework 2.5.1
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0xae03bd44fd00 Ph4nPy.readme.txt file.0xae03bd44fd00.0xae03b5a857a0.DataSectionObject.Ph4nPy.readme.txt.dat
$ cat file.0xae03bd44fd00.0xae03b5a857a0.DataSectionObject.Ph4nPy.readme.txt.dat
CiAgICBXb3cuLi4gWW91IGZvdW5kIHRoZSByZWFkbWUudHh0Li4uIEJ1dCBjYW4geW91IHNlZSB0aGUgd2FsbHBhcGVyID8KICAgIFNvbWV0aW1lcyB5b3UgbmVlZCB0byBmb2xsb3cgdGhlIHdhdGVyIGJlZm9yZSB0byBqdW1wIGluLgoKICAgIGFuZCBCVFcgOiBUaGlzIFBva2Vtb24gbGl2ZXMgYW5kIG5lc3RzIG9uIGEgcml2ZXJiYW5rLiBBZnRlciBwbGF5aW5nIGluIHRoZSBtdWQsIGl0IHdvbuKAmXQgYmUgYWJsZSB0byBzZXR0bGUgZG93biB1bmxlc3MgaXQgd2FzaGVzIGl0cyBib2R5LgogICAg
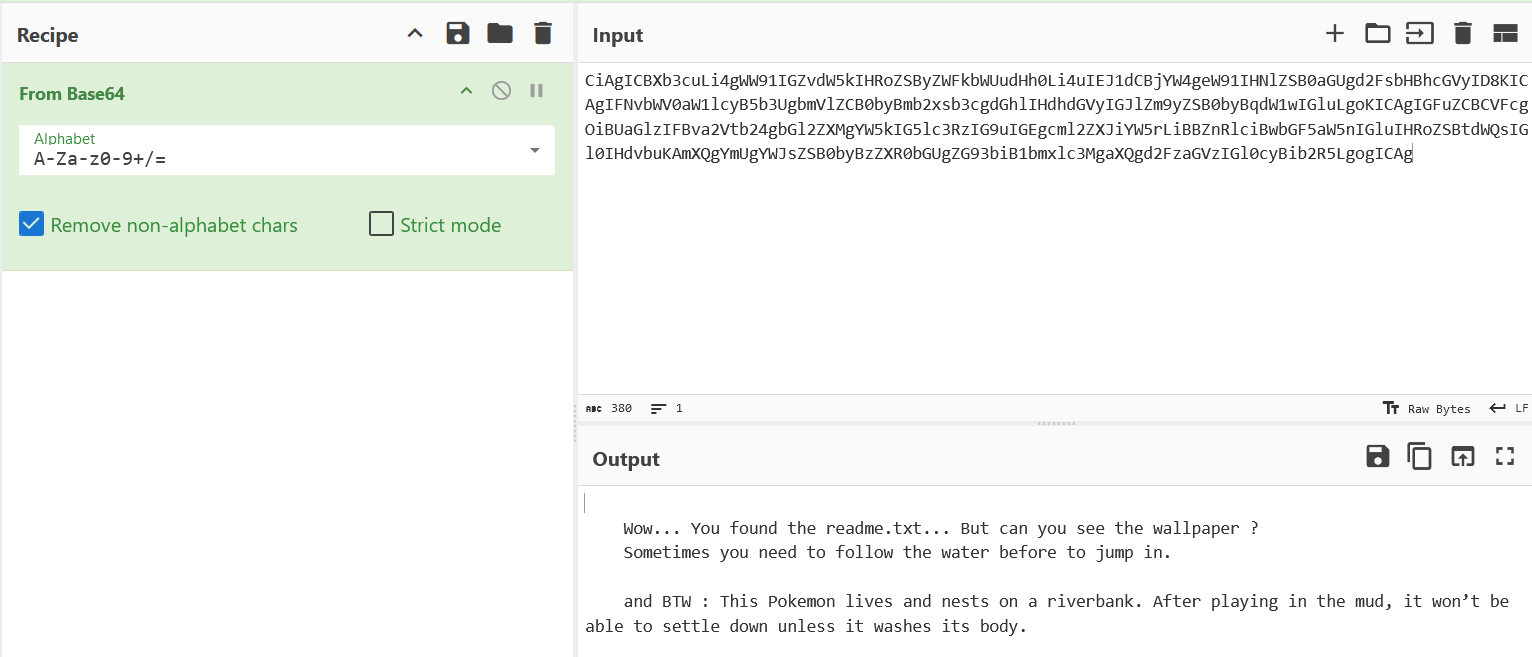
This gives us a good indication of what to look for next and how to direct our investigation.
We therefore go in search of the wallpaper placed by our malware on the victim machine.
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.filescan | grep -i wallpaper
0xae03bd45d310.0\Users\bipbop\AppData\Roaming\Microsoft\Windows\Themes\TranscodedWallpaper 216
to make sure that we are good we can double check with this page which gives us an idea of the possible paths
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem windows.dumpfiles --virtaddr 0xae03bd45d310
Volatility 3 Framework 2.5.1
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0xae03bd45d310 TranscodedWallpaper file.0xae03bd45d310.0xae03b5a85660.DataSectionObject.TranscodedWallpaper.dat
$ file file.0xae03bd45d310.0xae03b5a85660.DataSectionObject.TranscodedWallpaper.dat
file.0xae03bd45d310.0xae03b5a85660.DataSectionObject.TranscodedWallpaper.dat: JPEG image data, JFIF standard 1.01, resolution (DPI), density 96x96, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=1], baseline, precision 8, 687x447, components 3
$ mv file.0xae03bd45d310.0xae03b5a85660.DataSectionObject.TranscodedWallpaper.dat file.0xae03bd45d310.0xae03b5a85660.DataSectionObject.TranscodedWallpaper.dat.jpeg

ツ Fun fact
While getting lost in the memory capture during my analysis, I came across the symlinks of the Windows VM.
Allowing me to discover the identity of the challmaker 👀
$ python3 /home/shaym/volatility3/vol.py -f memdump.mem timeliner --plugin-filter symlinkscan --create-bodyfile > symlink.txt
$ cat symlink.txt |grep -i *******
SymlinkScan Symlink: T: -> \*****\*****\;T:\*****\********** ******* ********** N/A N/A N/A
I think this video and this tool would be of great help for creating future challenges
Thanks a lot for this challenge man, I really enjoyed solving it !




