Splunk - Boss of the SOC

📜Scenario 1 / Web Site Defacement
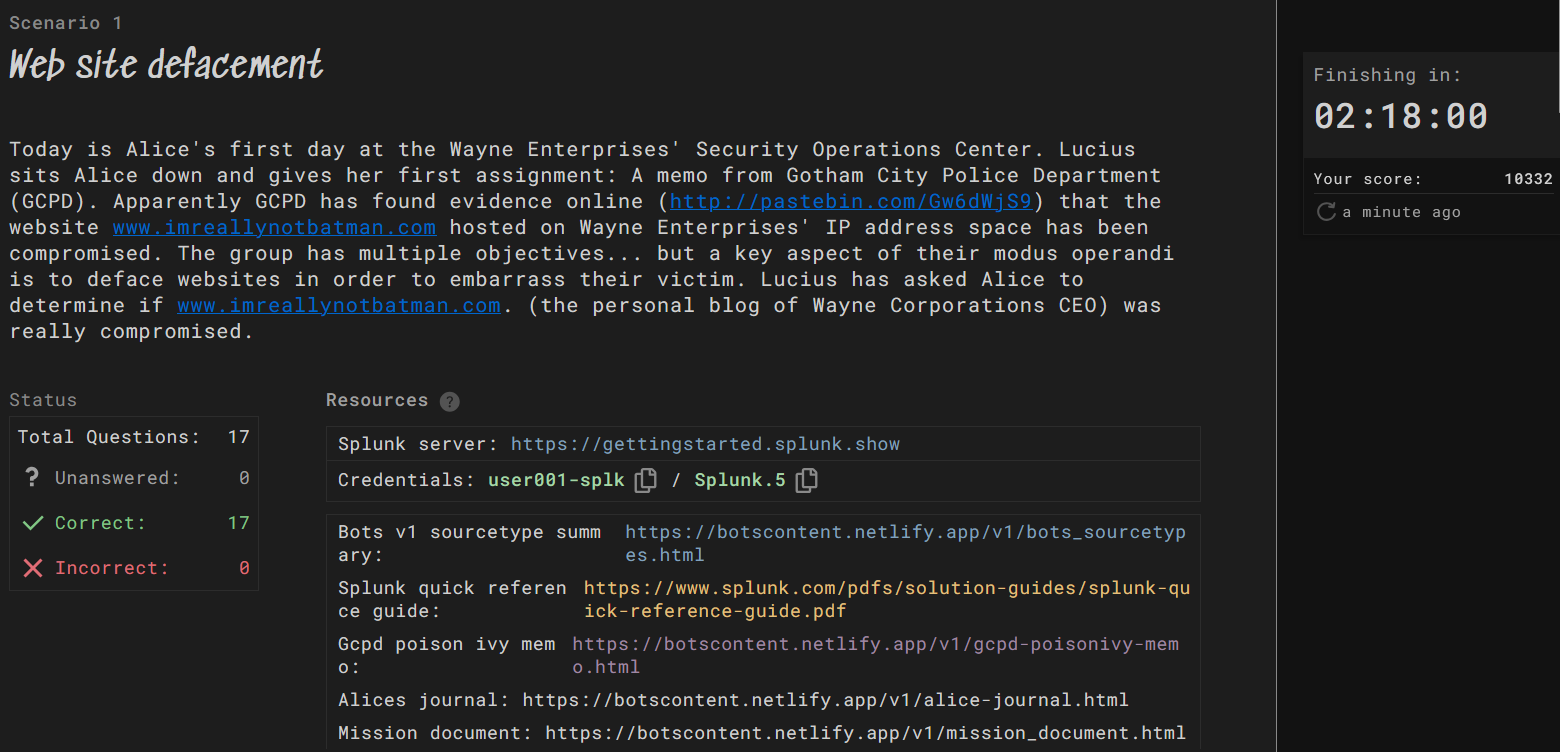
What is the likely IPv4 address of someone from the Po1s0n1vy group scanning imreallynotbatman.com for web application vulnerabilities?
imreallynotbatman.com
40.80.148.42
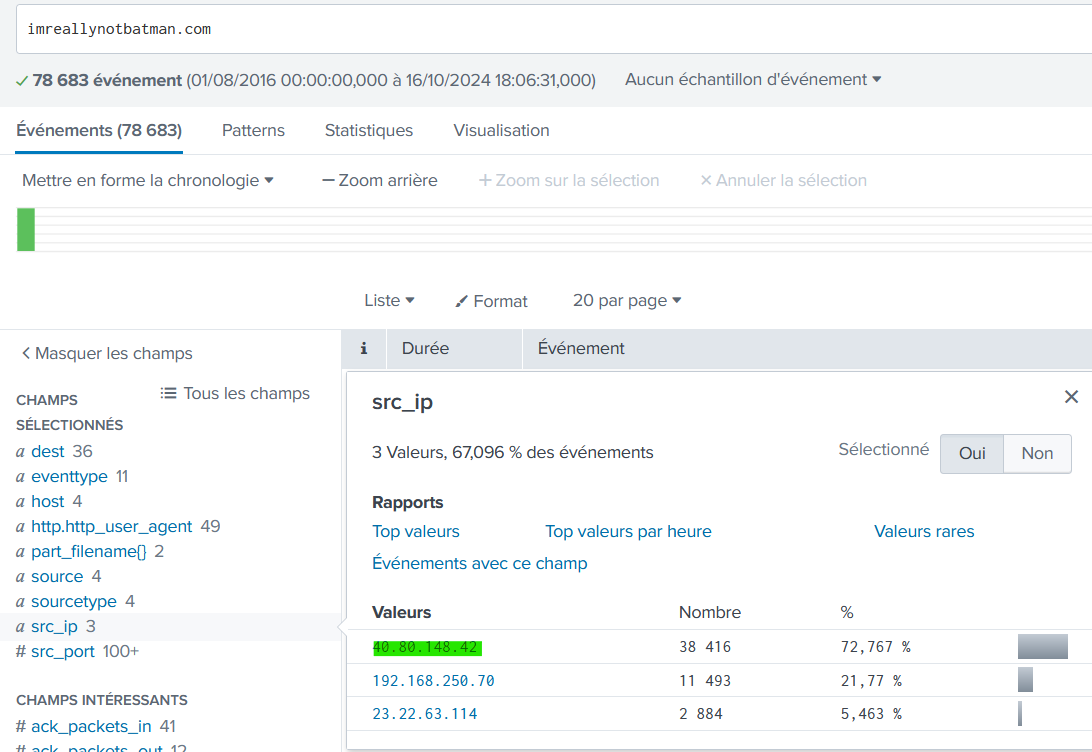
What company created the web vulnerability scanner used by Po1s0n1vy? Type the company name.
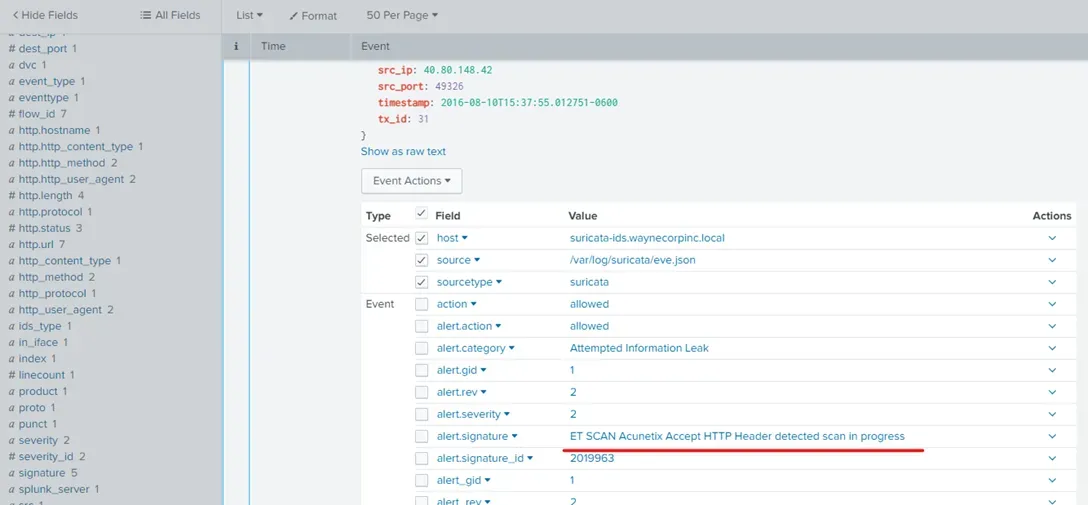
Acunetix
What content management system is imreallynotbatman.com likely using?
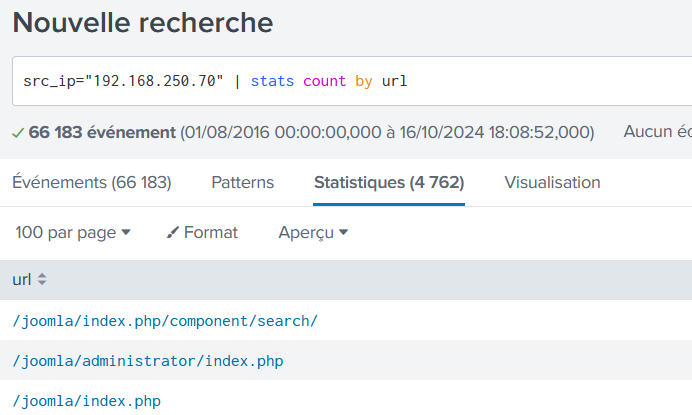
src_ip="192.168.250.70" | stats count by url
joomla
What is the name of the file that defaced the imreallynotbatman.com website? Please submit only the name of the file with extension?
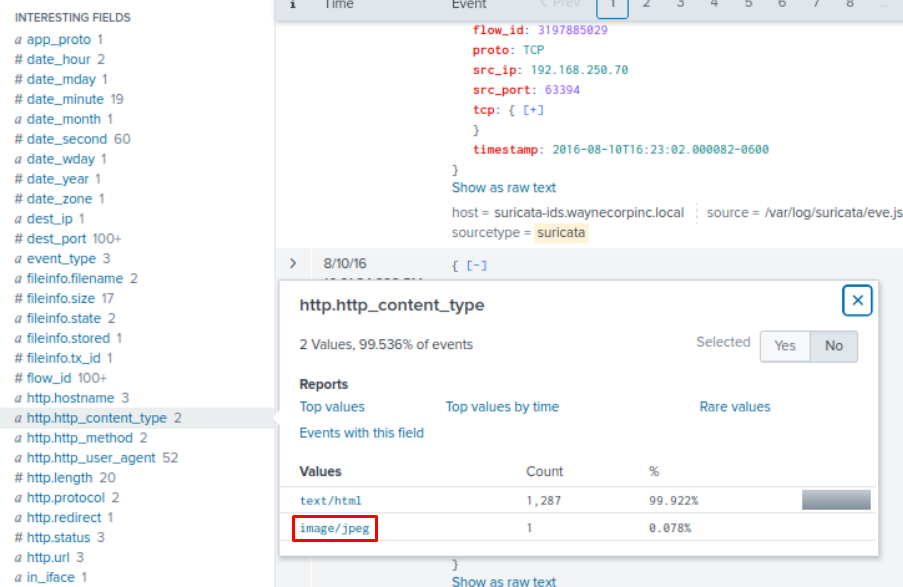
src_ip="192.168.250.70" "http.http_content_type"="image/jpeg" | stats count by url
/poisonivy-is-coming-for-you-batman.jpeg
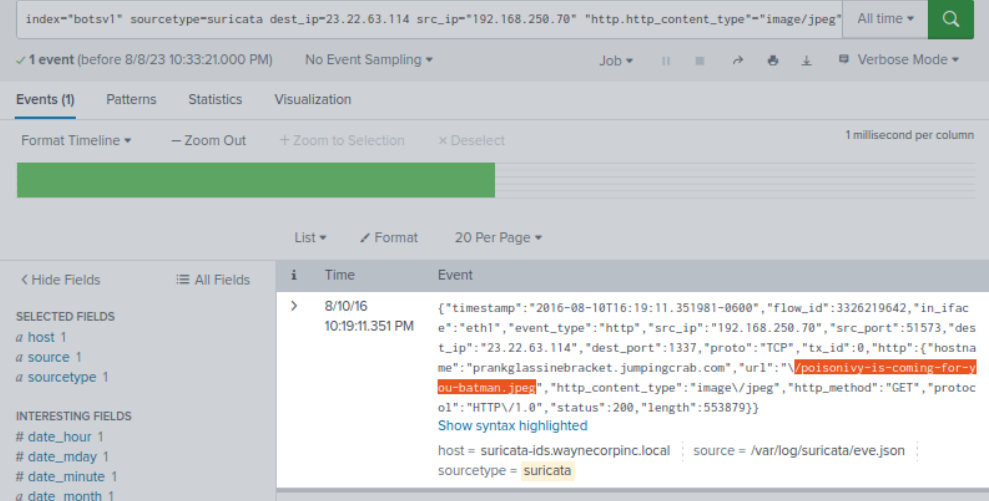
This attack used dynamic DNS to resolve to the malicious IP. What fully qualified domain name (FQDN) is associated with this attack?
src_ip="192.168.250.70" "http.http_content_type"="image/jpeg" | stats count by url
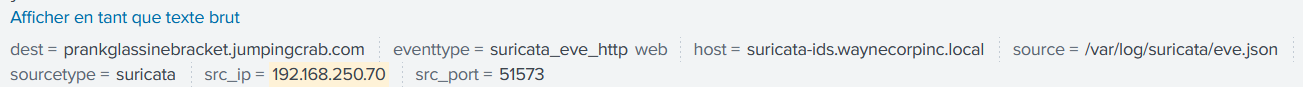
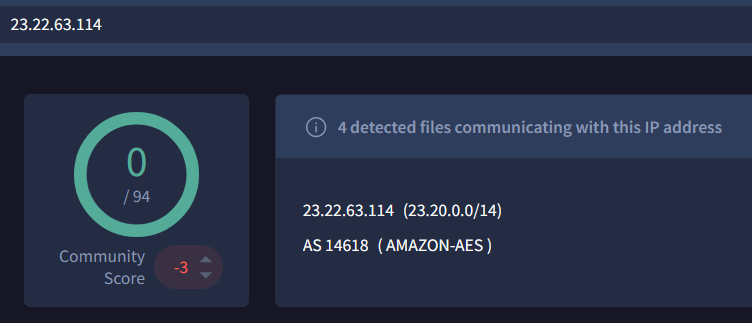
dest = prankglassinebracket.jumpingcrab.comWhat IPv4 address has Po1s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
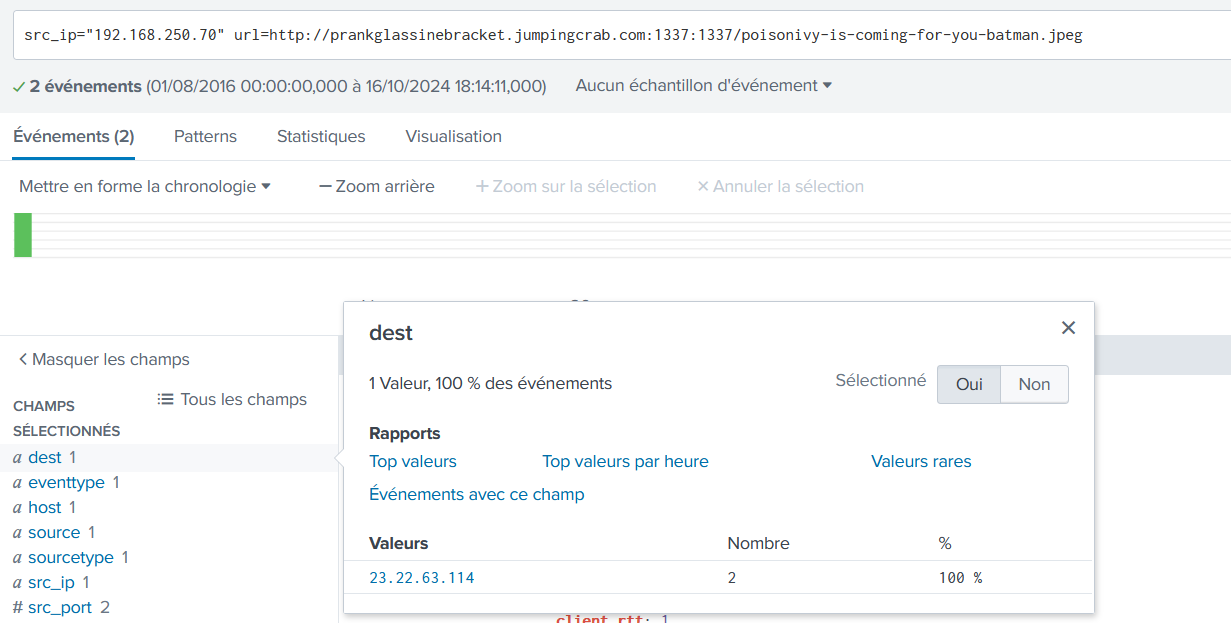
src_ip="192.168.250.70" url=http://prankglassinebracket.jumpingcrab.com:1337:1337/poisonivy-is-coming-for-you-batman.jpeg
23.22.63.114
What IPv4 address is likely attempting a brute force password attack against imreallynotbatman.com?
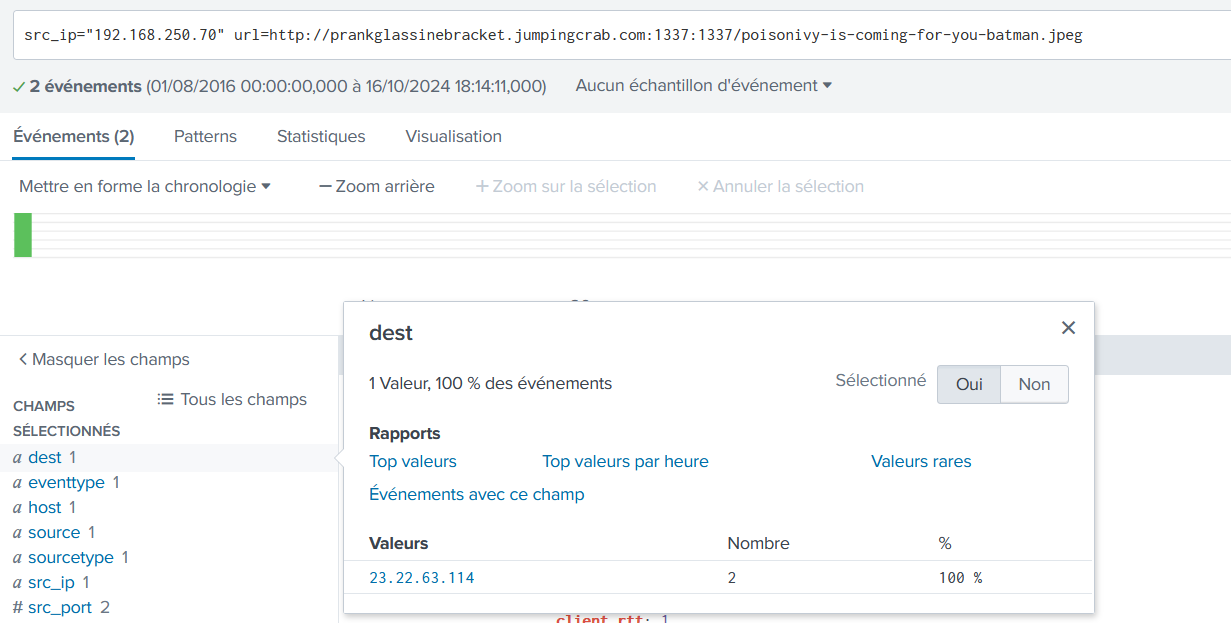
dest_ip="192.168.250.70" imreallynotbatman.com http_method=POST|stats count BY src, form_data, status
23.22.63.114
What is the name of the executable uploaded by Po1s0n1vy?
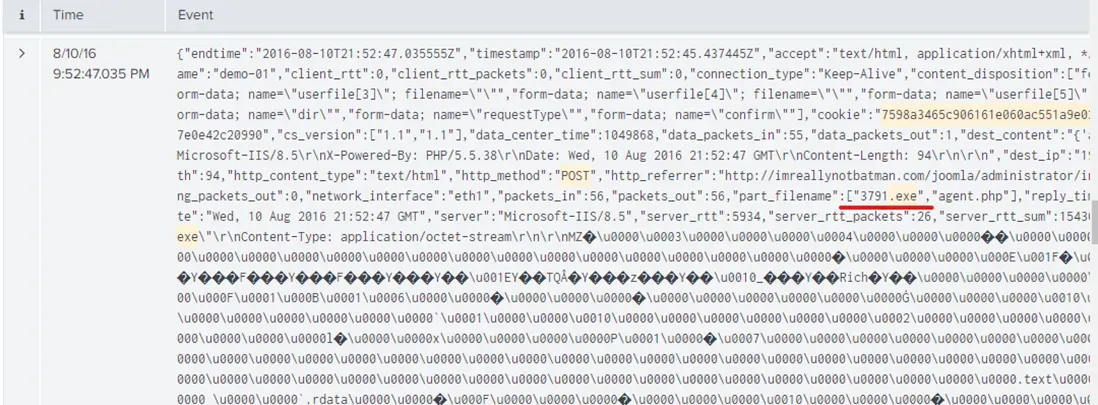
dest_ip="192.168.250.70" sourcetype="stream:http" POST *.exe
3791.exe
What is the MD5 hash of the executable uploaded?
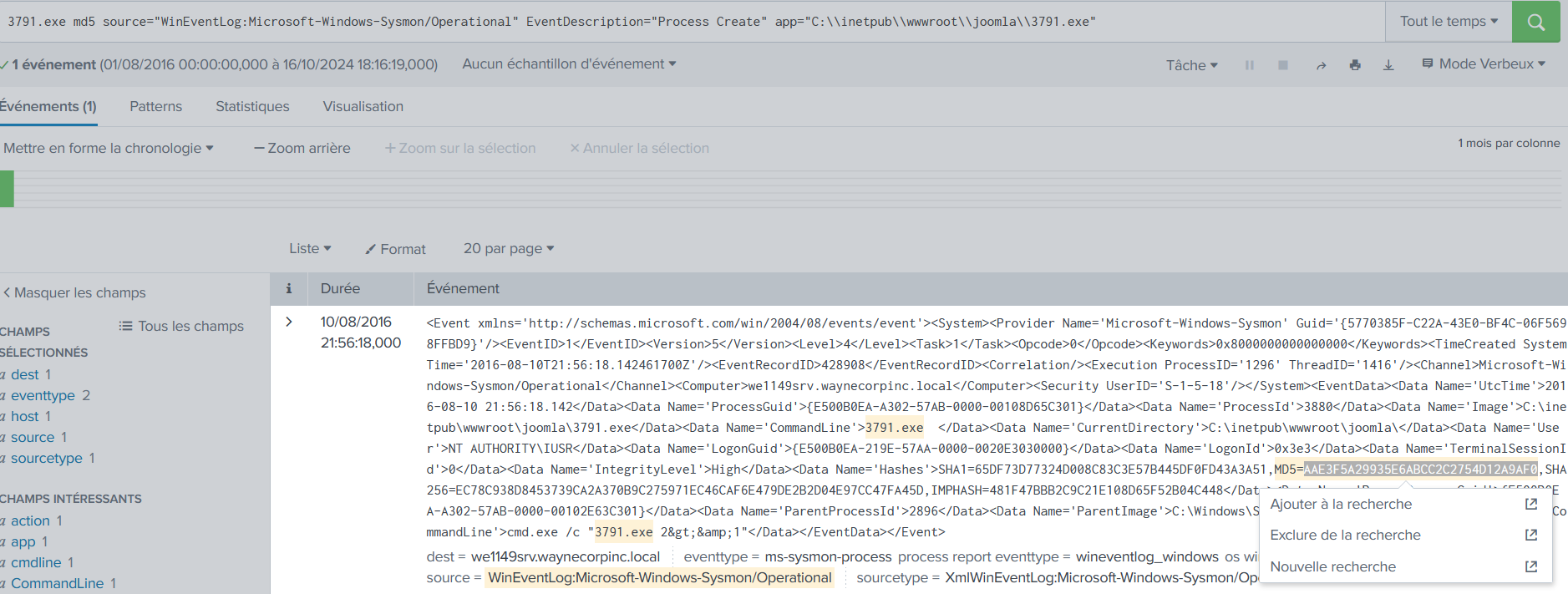
3791.exe md5 source="WinEventLog:Microsoft-Windows-Sysmon/Operational" EventDescription="Process Create" app="C:\\inetpub\\wwwroot\\joomla\\3791.exe"
AAE3F5A29935E6ABCC2C2754D12A9AF0
GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the Po1s0n1vy APT group, if initial compromise fails, is to send a spear phishing email with custom malware attached to their intended target. This malware is usually connected to Po1s0n1vys initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.
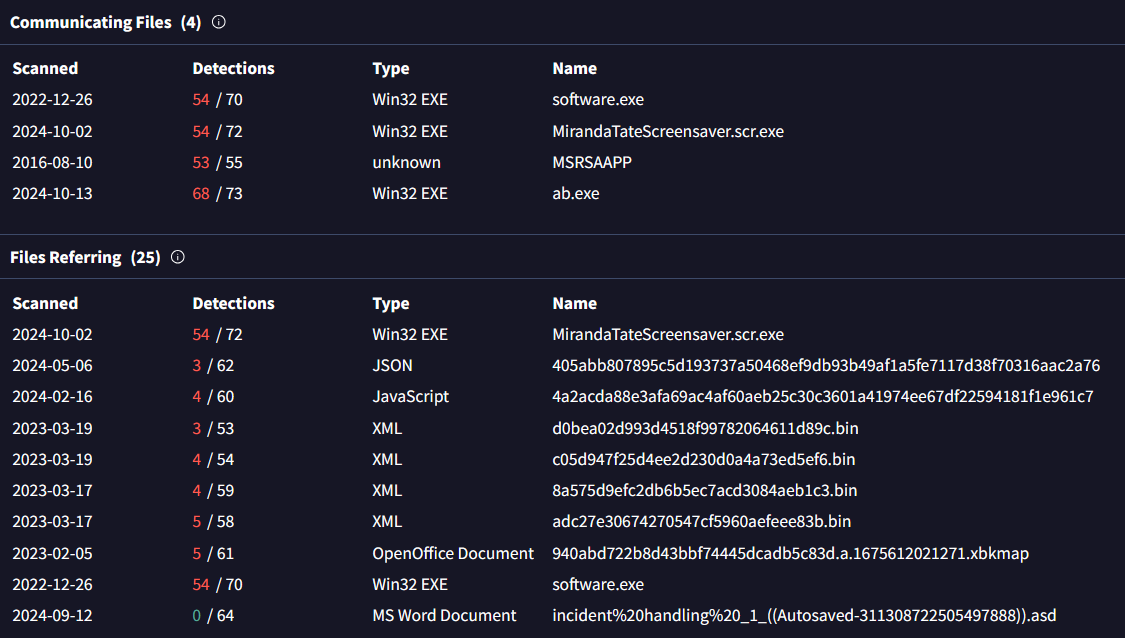
9709473ab351387aab9e816eff3910b9f28a7a70202e250ed46dba8f820f34a8
What special hex code is associated with the customized malware discussed in question 111?
53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21
What was the first brute force password used?
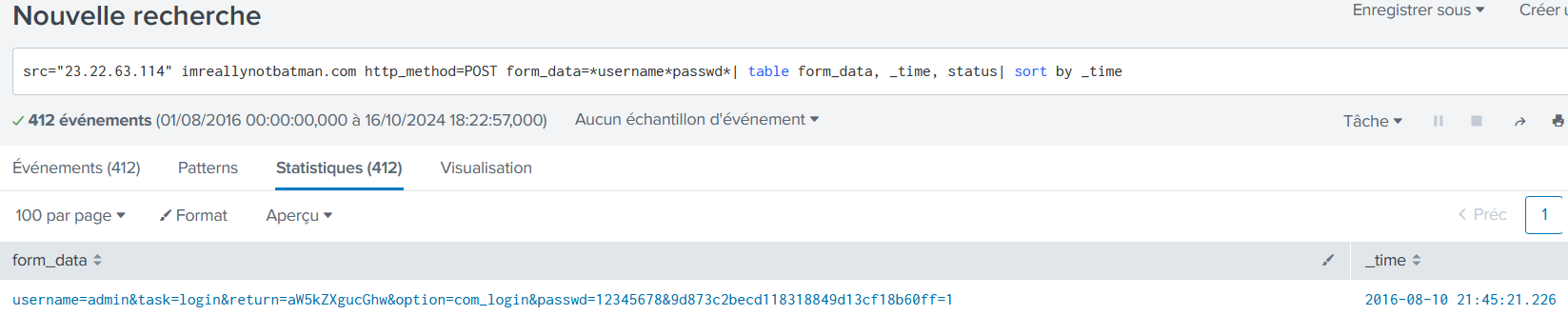
src="23.22.63.114" imreallynotbatman.com http_method=POST form_data=*username*passwd*| table form_data, _time, status| sort by _time
12345678
One of the passwords in the brute force attack is James Brodsky's favorite Coldplay song. We are looking for a six character word on this one. Which is it?
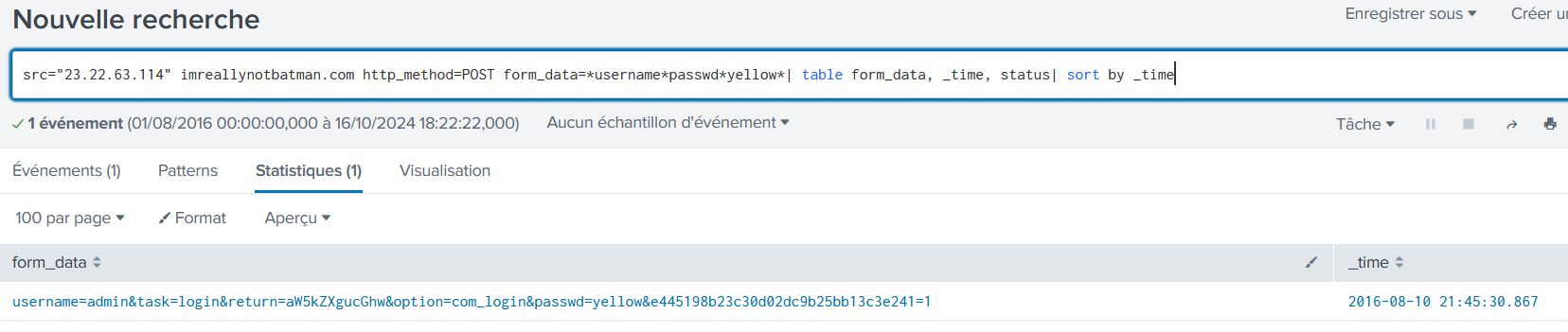
src="23.22.63.114" imreallynotbatman.com http_method=POST form_data=*username*passwd*yellow*| table form_data, _time, status| sort by _time
yellow
What was the correct password for admin access to the content management system running "imreallynotbatman.com"?
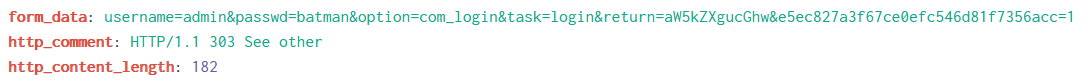
imreallynotbatman.com http_method=POST form_data="*username*passwd*" connection_type="Keep-Alive"
batman
What was the average password length used in the password brute forcing attempt?
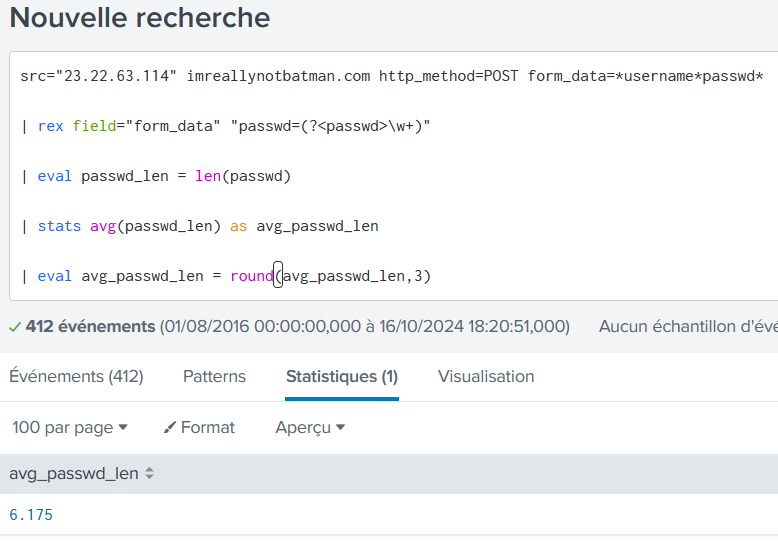
src="23.22.63.114" imreallynotbatman.com http_method=POST form_data=*username*passwd*
| rex field="form_data" "passwd=(?<passwd>\w+)"
| eval passwd_len = len(passwd)
| stats avg(passwd_len) as avg_passwd_len
| eval avg_passwd_len = round(avg_passwd_len,3)
6.175
How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login?
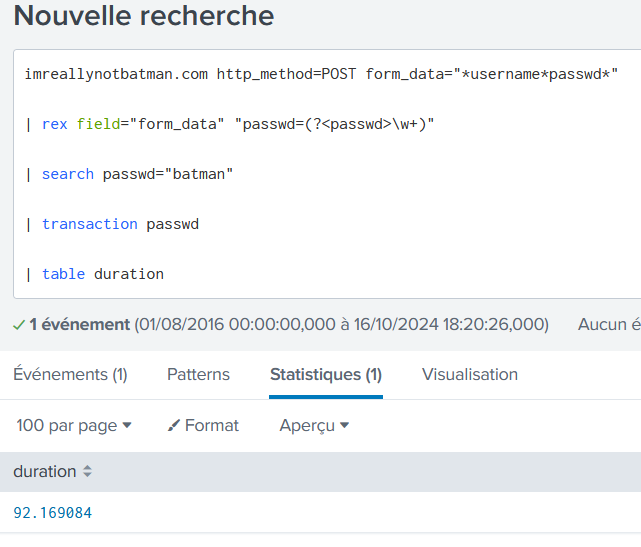
imreallynotbatman.com http_method=POST form_data="*username*passwd*"
| rex field="form_data" "passwd=(?<passwd>\w+)"
| search passwd="batman"
| transaction passwd
| table duration
92.169084
How many unique passwords were attempted in the brute force attempt?
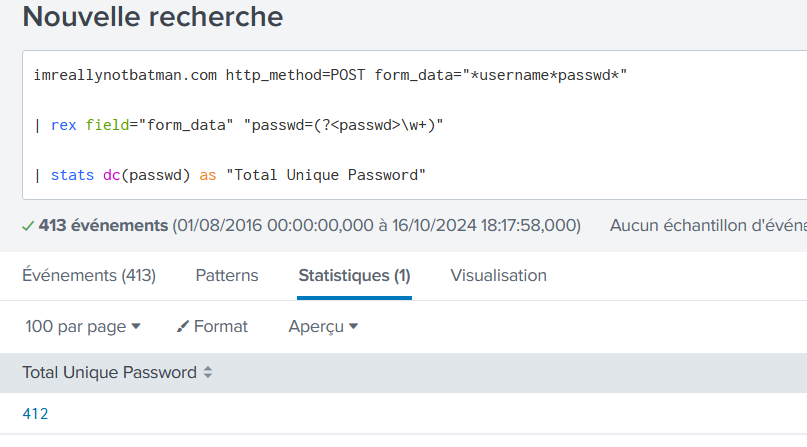
imreallynotbatman.com http_method=POST form_data="*username*passwd*"
| rex field="form_data" "passwd=(?<passwd>\w+)"
| stats dc(passwd) as "Total Unique Password"
412
📜Scenario 2 / Ransomware
What was the most likely IPv4 address of we8105desk on 24AUG2016?
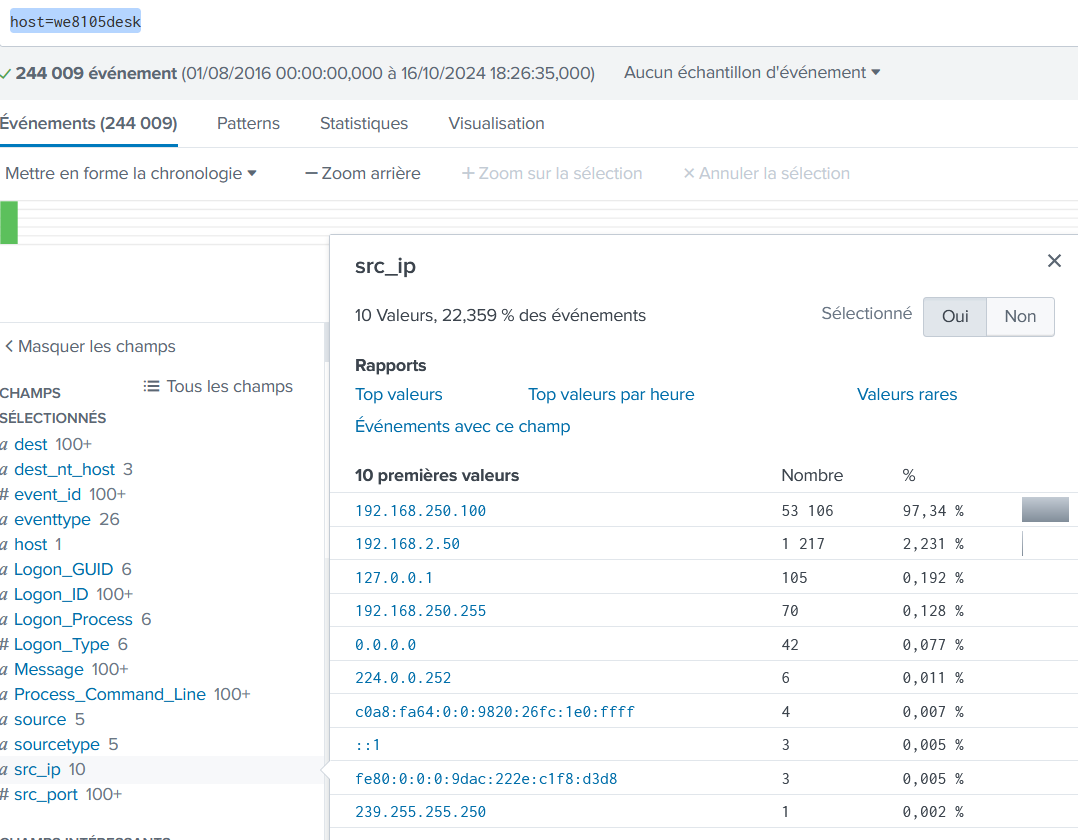
host=we8105desk
192.168.250.100
Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer.
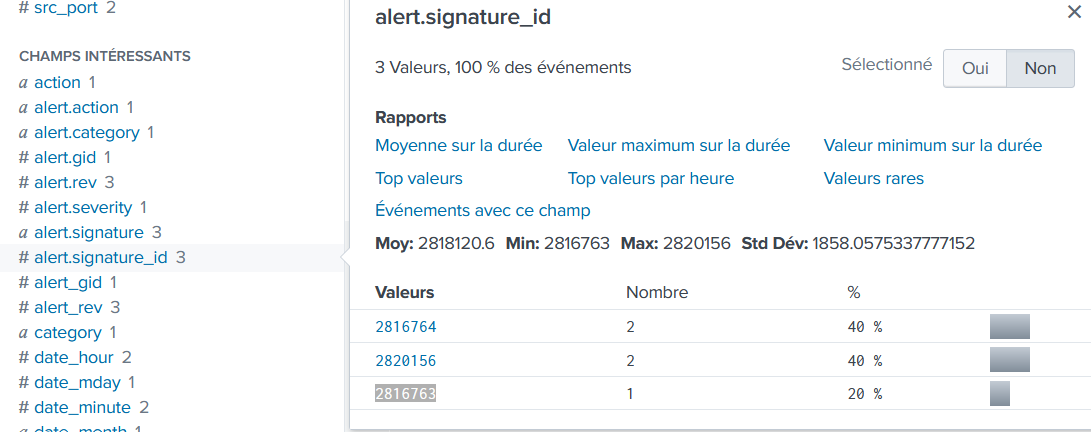
cerber host="suricata-ids.waynecorpinc.local"
2816763
What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?

source="stream:dns" src_ip="192.168.250.100" query!="*.arpa" | stats count by query
cerberhhyed5frqa.xmfir0.win
What was the first suspicious domain visited by we8105desk on 24AUG2016?

source="stream:dns" src_ip="192.168.250.100" NOT query IN ("*.arpa", "*.local", "*.microsft.com") AND query=*.* | table _time, query | sort _time
solidaritedeproximite.org
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length of the value of this field?
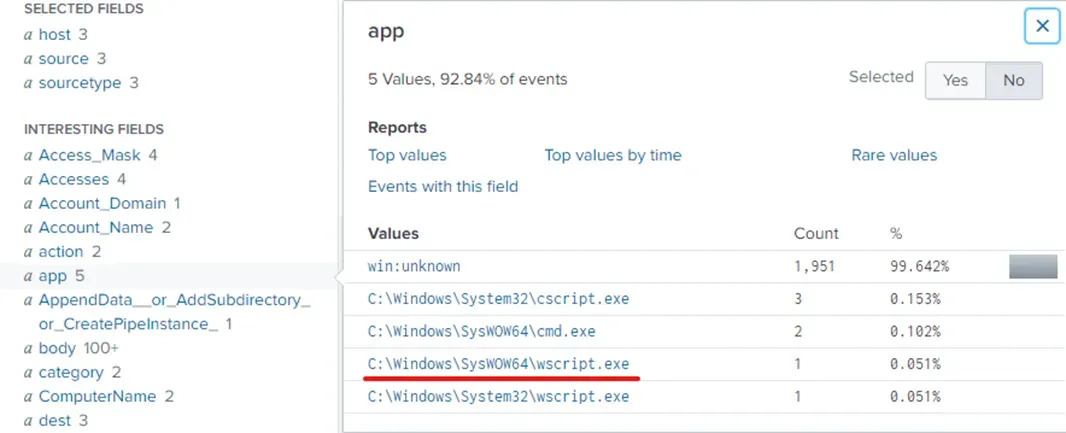
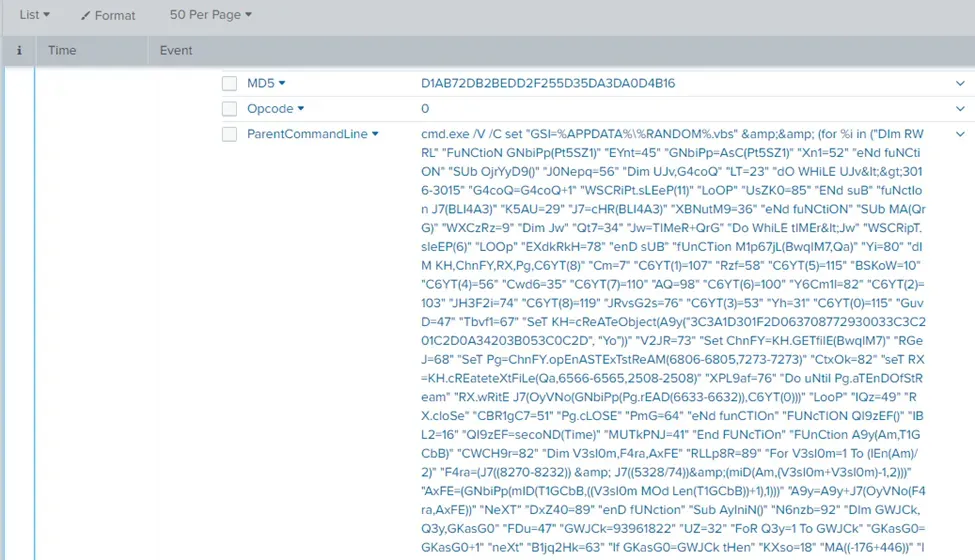
vbs app="C:\\Windows\\System32\\wscript.exe" | eval length=len(ParentCommandLine) | table length
4490
What is the name of the USB key inserted by Bob Smith?
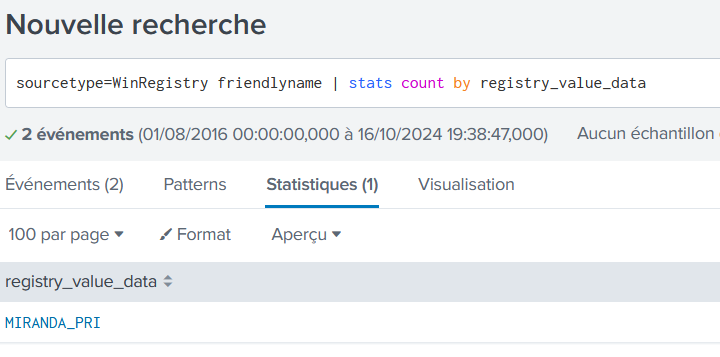
sourcetype=WinRegistry friendlyname | stats count by registry_value_data
MIRANDA_PRI
Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IPv4 address of the file server?
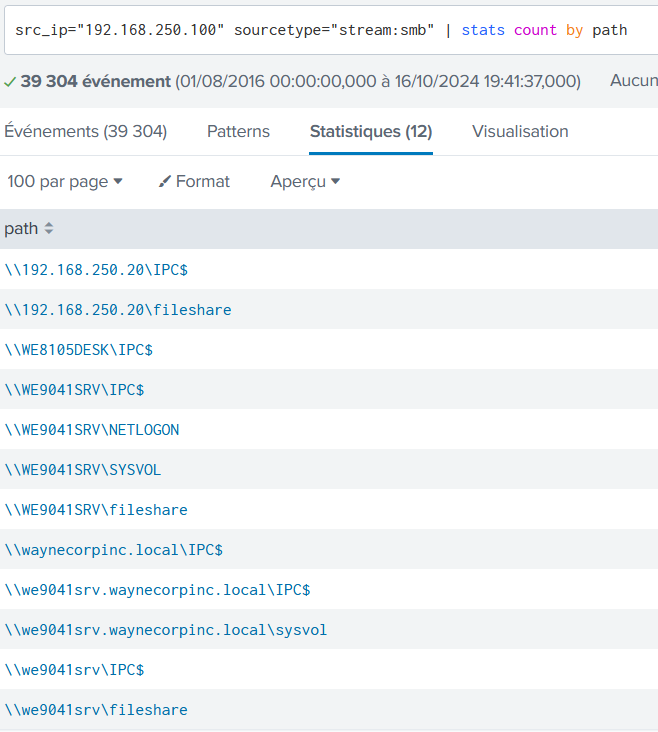
src_ip="192.168.250.100" sourcetype="stream:smb" | stats count by path
192.168.250.20
How many distinct PDFs did the ransomware encrypt on the remote file server?
*.pdf dvc=”we9041srv.waynecorpinc.local” | stats dc(Relative_Target_Name)
257
The VBscript found in question 204 launches 121214.tmp. What is the ParentProcessId of this initial launch?
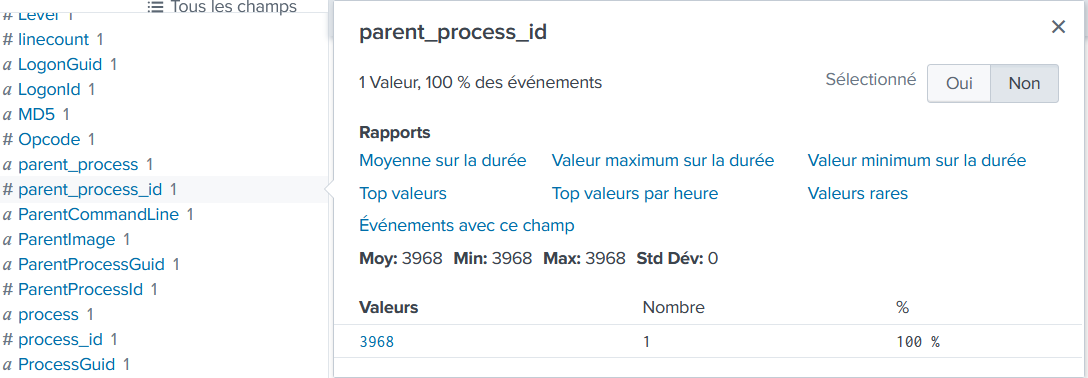
121214.tmp wscript
3968
The Cerber ransomware encrypts files located in Bob Smith's Windows profile. How many .txt files does it encrypt?
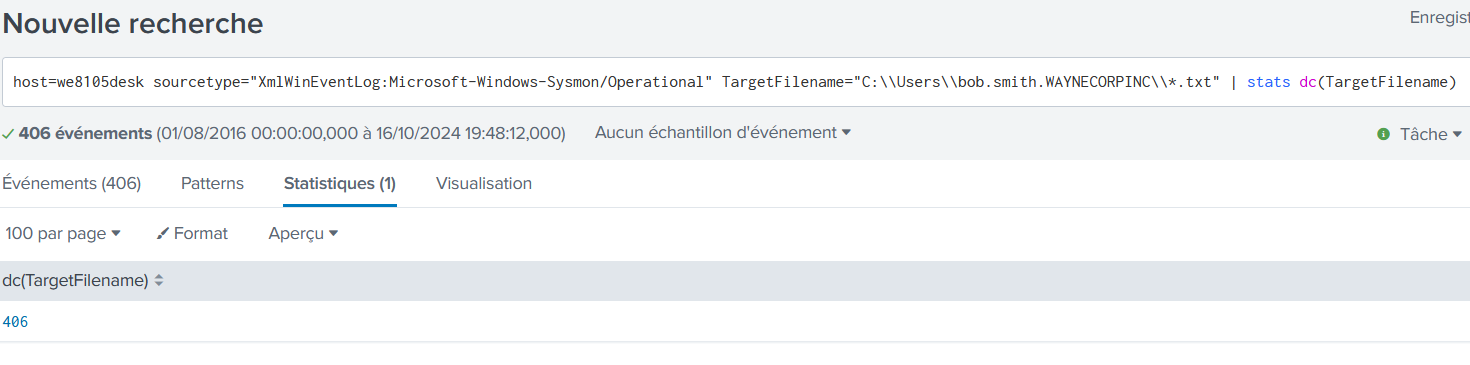
host=we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" TargetFilename="C:\\Users\\bob.smith.WAYNECORPINC\\*.txt" | stats dc(TargetFilename)
406
The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file?
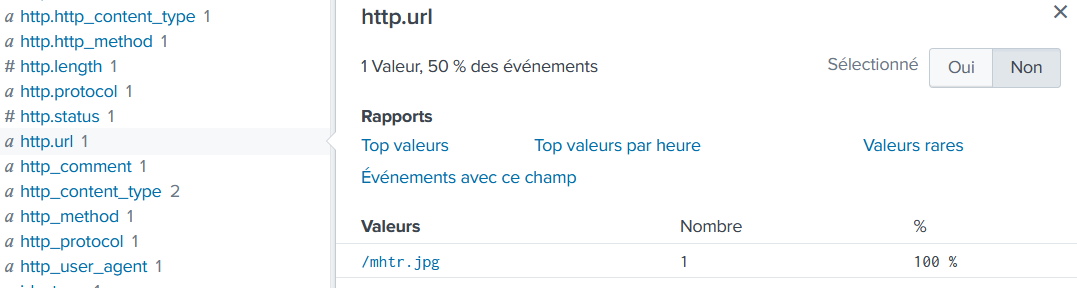
src_ip="192.168.250.100" "solidaritedeproximite.org" http_method="GET"
/mhtr.jpg
Now that you know the name of the ransomware's encryptor file, what obfuscation technique does it likely use?
steganographie
Conclusion
In this task I have learnt how to:
- Conduct search queries to find information in Splunk SIEM
- Find IOCs linked to APT activity
- Find marker of Ransomware activity
- Conduct research to find malware information
I was able to finish the scenario in 3h17 that was a really good and intense exercice
Thanks for reading.
Happy learning!




