Tin Balloon
📜Scenario
🔎Solve
We got a zip with an audio file and a Word file
First during the analyse of the audio file we notice some weird noise as always when the spectrogram of an audio is modified.
We display it with audacity, be careful the text is written the high frequency of the recording, so we need to zoom out (right click + adapted zoom) to display Ok-22k frequency.
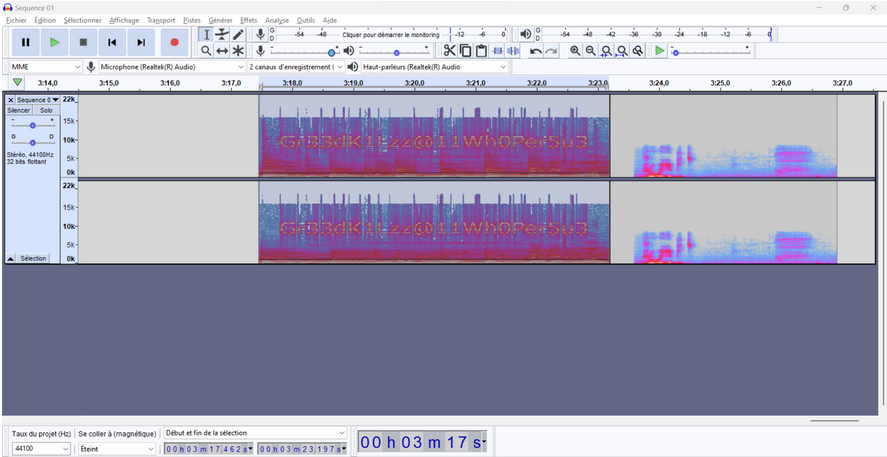
We got a passphrase :)
Now let take a look to the Word file :
$ file Untitlednosubject.docx
Untitlednosubject.docx: CDFV2 Encrypted
Google it a bit and find this doc. It explain the this file is not a classic Word document, it’s a CDFv2 or “Compound Document Format” but also encrypted as reported by the file command above. In general, antiviruses have more difficulty analyzing these documents due to the encryption of the data contained.
To make sure it's the right word we use john to crack the pass
$ python3 office2john.py Untitlednosubject.docx > docxhash.txt
$ john --wordlist=wordlist.txt docxhash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 256/256 AVX2 8x / SHA512 256/256 AVX2 4x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 1 candidate left, minimum 64 needed for performance.
Gr33dK1Lzz@11Wh0Per5u3 (Untitlednosubject.docx)
1g 0:00:00:01 DONE (2023-10-20 19:28) 0.6944g/s 0.6944p/s 0.6944c/s 0.6944C/s Gr33dK1Lzz@11Wh0Per5u3
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
All right !
Now we can decipher the Word document with this tool :
$ pip install msoffcrypto-tool
$ msoffcrypto-tool Untitlednosubject.docx decrypted.docx -p Gr33dK1Lzz@11Wh0Per5u3
$ binwalk -e decrypted.docx
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Zip archive data, at least v2.0 to extract, compressed size: 346, uncompressed size: 1312, name: [Content_Types].xml
915 0x393 Zip archive data, at least v2.0 to extract, compressed size: 239, uncompressed size: 590, name: _rels/.rels
1715 0x6B3 Zip archive data, at least v2.0 to extract, compressed size: 1051, uncompressed size: 3627, name: word/document.xml
2813 0xAFD Zip archive data, at least v2.0 to extract, compressed size: 244, uncompressed size: 817, name: word/_rels/document.xml.rels
3379 0xD33 Zip archive data, at least v2.0 to extract, compressed size: 1746, uncompressed size: 8393, name: word/theme/theme1.xml
5176 0x1438 Zip archive data, at least v2.0 to extract, compressed size: 1078, uncompressed size: 3103, name: word/settings.xml
6301 0x189D Zip archive data, at least v2.0 to extract, compressed size: 2947, uncompressed size: 29455, name: word/styles.xml
9293 0x244D Zip archive data, at least v2.0 to extract, compressed size: 334, uncompressed size: 894, name: word/webSettings.xml
9677 0x25CD Zip archive data, at least v2.0 to extract, compressed size: 495, uncompressed size: 1658, name: word/fontTable.xml
10220 0x27EC Zip archive data, at least v2.0 to extract, compressed size: 374, uncompressed size: 751, name: docProps/core.xml
10905 0x2A99 Zip archive data, at least v2.0 to extract, compressed size: 474, uncompressed size: 989, name: docProps/app.xml
12394 0x306A End of Zip archive, footer length: 22
After extracting the data from the Word document, we just need to check the contents of the file _decrypted.docx.extracted/word/document.xml
$ cat _decrypted.docx.extracted/word/document.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<w:document xmlns:wpc="http://schemas.microsoft.com/office/word/2010/wordprocessingCanvas" xmlns:cx="http://schemas.microsoft.com/office/drawing/2014/chartex" xmlns:cx1="http://schemas.microsoft.com/office/drawing/2015/9/8/chartex" xmlns:cx2="http://schemas.microsoft.com/office/drawing/2015/10/21/chartex" xmlns:cx3="http://schemas.microsoft.com/office/drawing/2016/5/9/chartex" xmlns:cx4="http://schemas.microsoft.com/office/drawing/2016/5/10/chartex" xmlns:cx5="http://schemas.microsoft.com/office/drawing/2016/5/11/chartex" xmlns:cx6="http://schemas.microsoft.com/office/drawing/2016/5/12/chartex" xmlns:cx7="http://schemas.microsoft.com/office/drawing/2016/5/13/chartex" xmlns:cx8="http://schemas.microsoft.com/office/drawing/2016/5/14/chartex" xmlns:mc="http://schemas.openxmlformats.org/markup-compatibility/2006" xmlns:aink="http://schemas.microsoft.com/office/drawing/2016/ink" xmlns:am3d="http://schemas.microsoft.com/office/drawing/2017/model3d" xmlns:o="urn:schemas-microsoft-com:office:office" xmlns:oel="http://schemas.microsoft.com/office/2019/extlst" xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships" xmlns:m="http://schemas.openxmlformats.org/officeDocument/2006/math" xmlns:v="urn:schemas-microsoft-com:vml" xmlns:wp14="http://schemas.microsoft.com/office/word/2010/wordprocessingDrawing" xmlns:wp="http://schemas.openxmlformats.org/drawingml/2006/wordprocessingDrawing" xmlns:w10="urn:schemas-microsoft-com:office:word" xmlns:w="http://schemas.openxmlformats.org/wordprocessingml/2006/main" xmlns:w14="http://schemas.microsoft.com/office/word/2010/wordml" xmlns:w15="http://schemas.microsoft.com/office/word/2012/wordml" xmlns:w16cex="http://schemas.microsoft.com/office/word/2018/wordml/cex" xmlns:w16cid="http://schemas.microsoft.com/office/word/2016/wordml/cid" xmlns:w16="http://schemas.microsoft.com/office/word/2018/wordml" xmlns:w16sdtdh="http://schemas.microsoft.com/office/word/2020/wordml/sdtdatahash" xmlns:w16se="http://schemas.microsoft.com/office/word/2015/wordml/symex" xmlns:wpg="http://schemas.microsoft.com/office/word/2010/wordprocessingGroup" xmlns:wpi="http://schemas.microsoft.com/office/word/2010/wordprocessingInk" xmlns:wne="http://schemas.microsoft.com/office/word/2006/wordml" xmlns:wps="http://schemas.microsoft.com/office/word/2010/wordprocessingShape" mc:Ignorable="w14 w15 w16se w16cid w16 w16cex w16sdtdh wp14">
<w:body>
<w:p w14:paraId="797E9D34" w14:textId="53CADDB1" w:rsidR="006729CB" w:rsidRDefault="00BE6DCC">
<w:r>
<w:t xml:space="preserve">We have the ID card of one the </w:t>
</w:r>
<w:proofErr w:type="gramStart"/>
<w:r>
<w:t>brand new</w:t>
</w:r>
<w:proofErr w:type="gramEnd"/>
<w:r>
<w:t xml:space="preserve"> employees Alejandro, We now know the location of Techno Global, we have a man on sight that has been tailing him. We believe we can get into the facility at 3 am. </w:t>
</w:r>
</w:p>
<w:p w14:paraId="459FFE43" w14:textId="40E2EAF0" w:rsidR="00BE6DCC" w:rsidRDefault="00BE6DCC">
<w:r>
<w:t xml:space="preserve">We don’t know how long we can have a foothold on the </w:t>
</w:r>
<w:proofErr w:type="gramStart"/>
<w:r>
<w:t>system</w:t>
</w:r>
<w:proofErr w:type="gramEnd"/>
<w:r>
<w:t xml:space="preserve"> but we are going to use Wh1t3_N01Z3.exe to sent out a reverse shell. Be prepared to listen for the signal. </w:t>
</w:r>
</w:p>
<w:sectPr w:rsidR="00BE6DCC">
<w:pgSz w:w="12240" w:h="15840"/>
<w:pgMar w:top="1440" w:right="1440" w:bottom="1440" w:left="1440" w:header="720" w:footer="720" w:gutter="0"/>
<w:cols w:space="720"/>
<w:docGrid w:linePitch="360"/>
</w:sectPr>
</w:body>
</w:document>
We can easily extract the text from the Word file as follow
"We don’t know how long we can have a foothold on the system but we are going to use Wh1t3_N01Z3.exe to sent out a reverse shell. Be prepared to listen for the signal."
So we get the following flag : flag{Wh1t3_N01Z3.exe}
WriteUp made by Shaym





